6.3.4 Implement Intrusion Prevention - 6.4.4 implement intrusion prevention complete this lab as follows: 6.4 intrusion detection and prevention. In an effort to protect your network against security threats. 6.3.1 intrusion detection (4:53) 6.3.2 ids facts; 6.4.1 intrusion detection and prevention (4:38) 6.4.2. Sign in to the pfsense.
6.3.1 intrusion detection (4:53) 6.3.2 ids facts; 6.4.4 implement intrusion prevention complete this lab as follows: In an effort to protect your network against security threats. 6.4 intrusion detection and prevention. Sign in to the pfsense. 6.4.1 intrusion detection and prevention (4:38) 6.4.2.
6.4.4 implement intrusion prevention complete this lab as follows: In an effort to protect your network against security threats. 6.4 intrusion detection and prevention. 6.4.1 intrusion detection and prevention (4:38) 6.4.2. 6.3.1 intrusion detection (4:53) 6.3.2 ids facts; Sign in to the pfsense.
Examples of Intrusion Prevention Systems (10 Best IPS Solutions)
6.3.1 intrusion detection (4:53) 6.3.2 ids facts; 6.4.1 intrusion detection and prevention (4:38) 6.4.2. In an effort to protect your network against security threats. Sign in to the pfsense. 6.4.4 implement intrusion prevention complete this lab as follows:
Intrusion Prevention System Go Nimbus
6.4 intrusion detection and prevention. 6.4.4 implement intrusion prevention complete this lab as follows: 6.4.1 intrusion detection and prevention (4:38) 6.4.2. In an effort to protect your network against security threats. 6.3.1 intrusion detection (4:53) 6.3.2 ids facts;
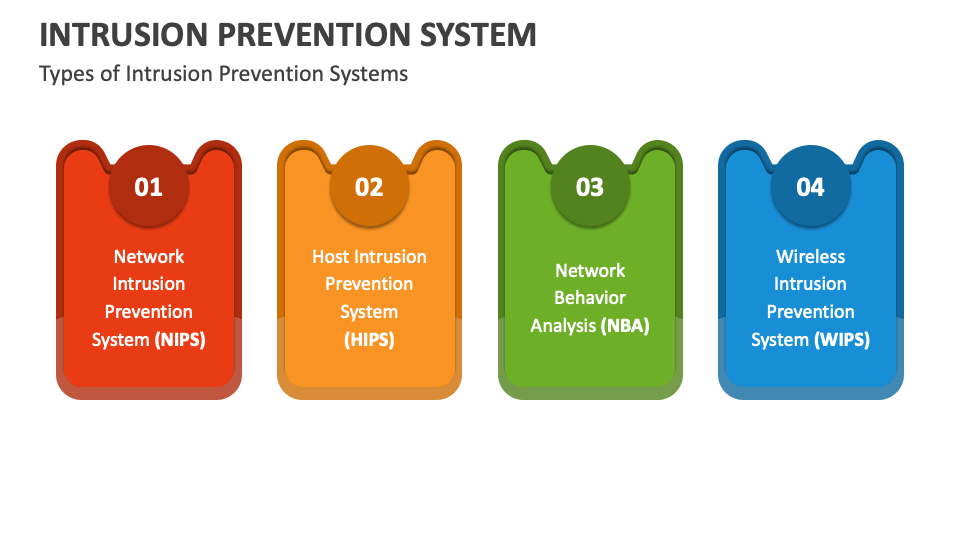
Intrusion Prevention System PPT Free Download
Sign in to the pfsense. 6.4.4 implement intrusion prevention complete this lab as follows: 6.4.1 intrusion detection and prevention (4:38) 6.4.2. 6.4 intrusion detection and prevention. In an effort to protect your network against security threats.
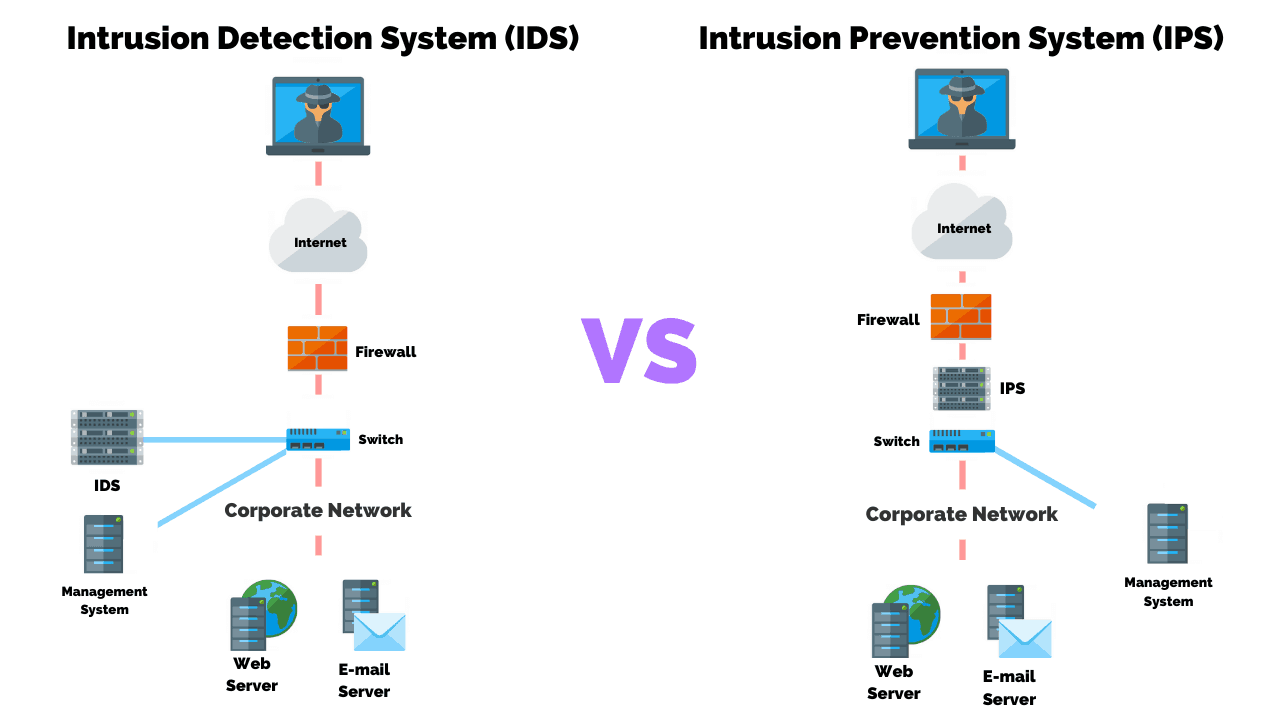
Intrusion Detection Systems vs. Intrusion Prevention Systems Which Is
6.4.1 intrusion detection and prevention (4:38) 6.4.2. Sign in to the pfsense. 6.4.4 implement intrusion prevention complete this lab as follows: 6.3.1 intrusion detection (4:53) 6.3.2 ids facts; In an effort to protect your network against security threats.
Intrusion Prevention System PowerPoint and Google Slides Template PPT
6.4.4 implement intrusion prevention complete this lab as follows: 6.4 intrusion detection and prevention. 6.3.1 intrusion detection (4:53) 6.3.2 ids facts; In an effort to protect your network against security threats. 6.4.1 intrusion detection and prevention (4:38) 6.4.2.
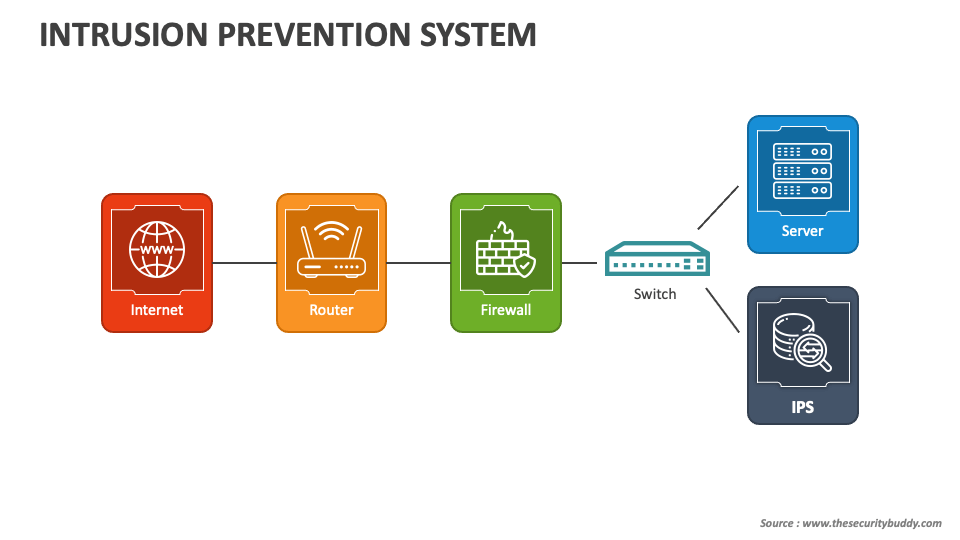
How to Implement an Intrusion Prevention System Enterprise Systems
6.4.1 intrusion detection and prevention (4:38) 6.4.2. 6.4 intrusion detection and prevention. In an effort to protect your network against security threats. 6.4.4 implement intrusion prevention complete this lab as follows: Sign in to the pfsense.
Intrusion Prevention System PowerPoint and Google Slides Template PPT
6.4.1 intrusion detection and prevention (4:38) 6.4.2. Sign in to the pfsense. 6.4.4 implement intrusion prevention complete this lab as follows: 6.4 intrusion detection and prevention. In an effort to protect your network against security threats.
Intrusion Detection VS Prevention Systems What's The Difference?
6.4 intrusion detection and prevention. In an effort to protect your network against security threats. 6.3.1 intrusion detection (4:53) 6.3.2 ids facts; 6.4.4 implement intrusion prevention complete this lab as follows: Sign in to the pfsense.
How to Implement an Intrusion Prevention System (IPS) to Boost Your
6.4.1 intrusion detection and prevention (4:38) 6.4.2. In an effort to protect your network against security threats. 6.4.4 implement intrusion prevention complete this lab as follows: 6.4 intrusion detection and prevention. Sign in to the pfsense.
SOLUTION 6 4 4 implement intrusion prevention lab Studypool
6.4 intrusion detection and prevention. 6.4.1 intrusion detection and prevention (4:38) 6.4.2. 6.4.4 implement intrusion prevention complete this lab as follows: In an effort to protect your network against security threats. 6.3.1 intrusion detection (4:53) 6.3.2 ids facts;
6.4.4 Implement Intrusion Prevention Complete This Lab As Follows:
6.3.1 intrusion detection (4:53) 6.3.2 ids facts; Sign in to the pfsense. 6.4.1 intrusion detection and prevention (4:38) 6.4.2. 6.4 intrusion detection and prevention.