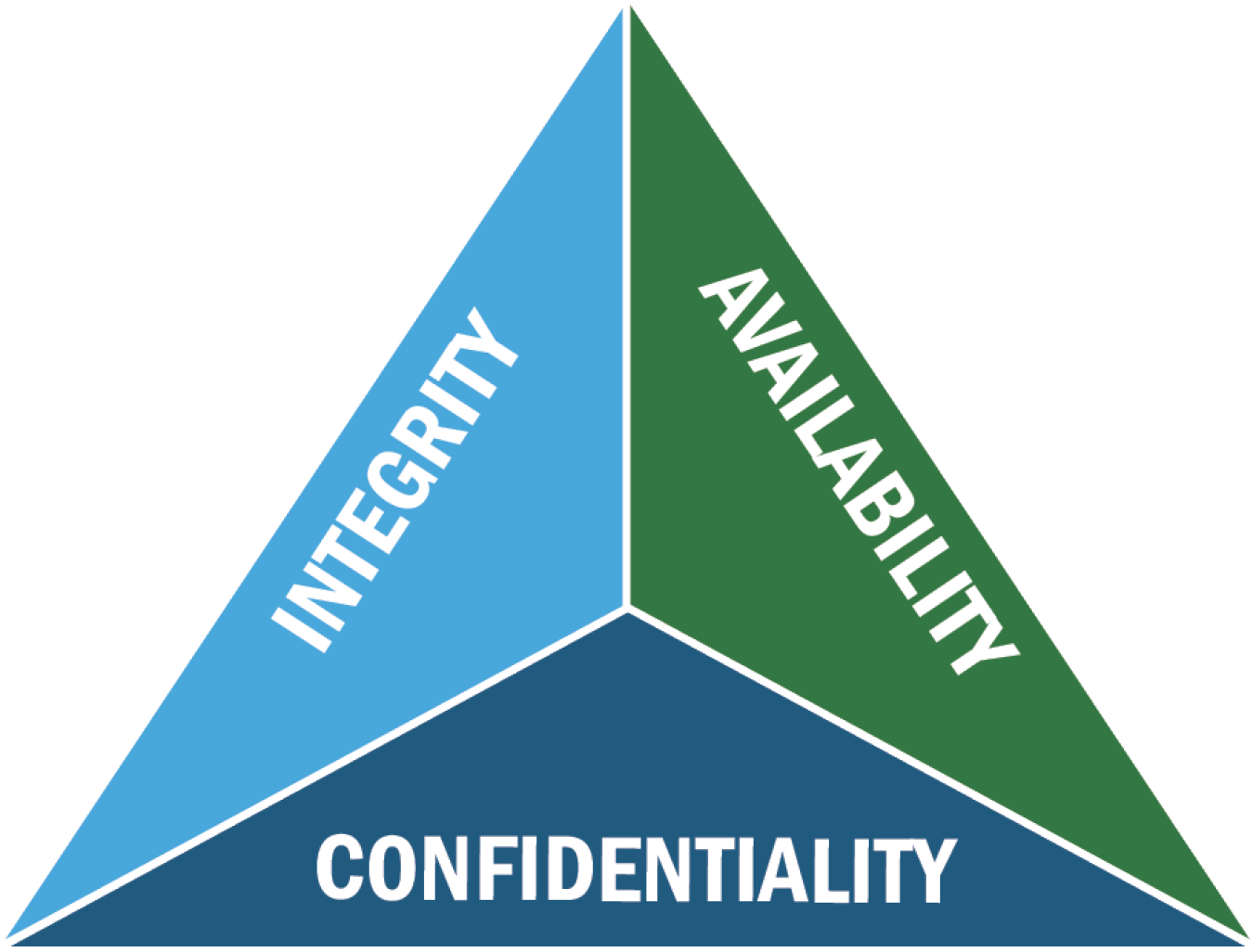
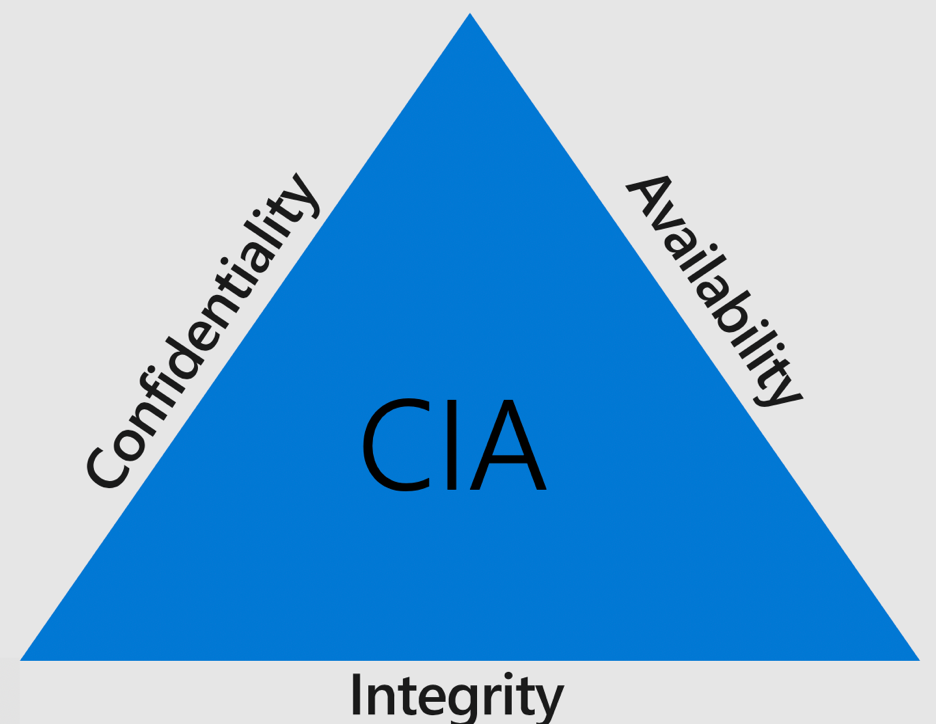
Confidentiality Integrity Availability - Learn how to protect information from unauthorized access, alteration, and loss with the cia triad model. The web page explains the.
The web page explains the. Learn how to protect information from unauthorized access, alteration, and loss with the cia triad model.
The web page explains the. Learn how to protect information from unauthorized access, alteration, and loss with the cia triad model.
Confidentiality Integrity Availability
Learn how to protect information from unauthorized access, alteration, and loss with the cia triad model. The web page explains the.
Confidentiality Integrity Availability
The web page explains the. Learn how to protect information from unauthorized access, alteration, and loss with the cia triad model.
Confidentiality, Integrity And Availability Confidentiality Integrity
The web page explains the. Learn how to protect information from unauthorized access, alteration, and loss with the cia triad model.
Confidentiality Integrity Availability
Learn how to protect information from unauthorized access, alteration, and loss with the cia triad model. The web page explains the.
Confidentiality Integrity Availability
Learn how to protect information from unauthorized access, alteration, and loss with the cia triad model. The web page explains the.
Confidentiality Integrity Availability
Learn how to protect information from unauthorized access, alteration, and loss with the cia triad model. The web page explains the.
2Confidentiality Integrity Availability PDF Information Security
Learn how to protect information from unauthorized access, alteration, and loss with the cia triad model. The web page explains the.
Confidentiality Integrity Availability
Learn how to protect information from unauthorized access, alteration, and loss with the cia triad model. The web page explains the.
Confidentiality Integrity Availability
Learn how to protect information from unauthorized access, alteration, and loss with the cia triad model. The web page explains the.
The Web Page Explains The.
Learn how to protect information from unauthorized access, alteration, and loss with the cia triad model.