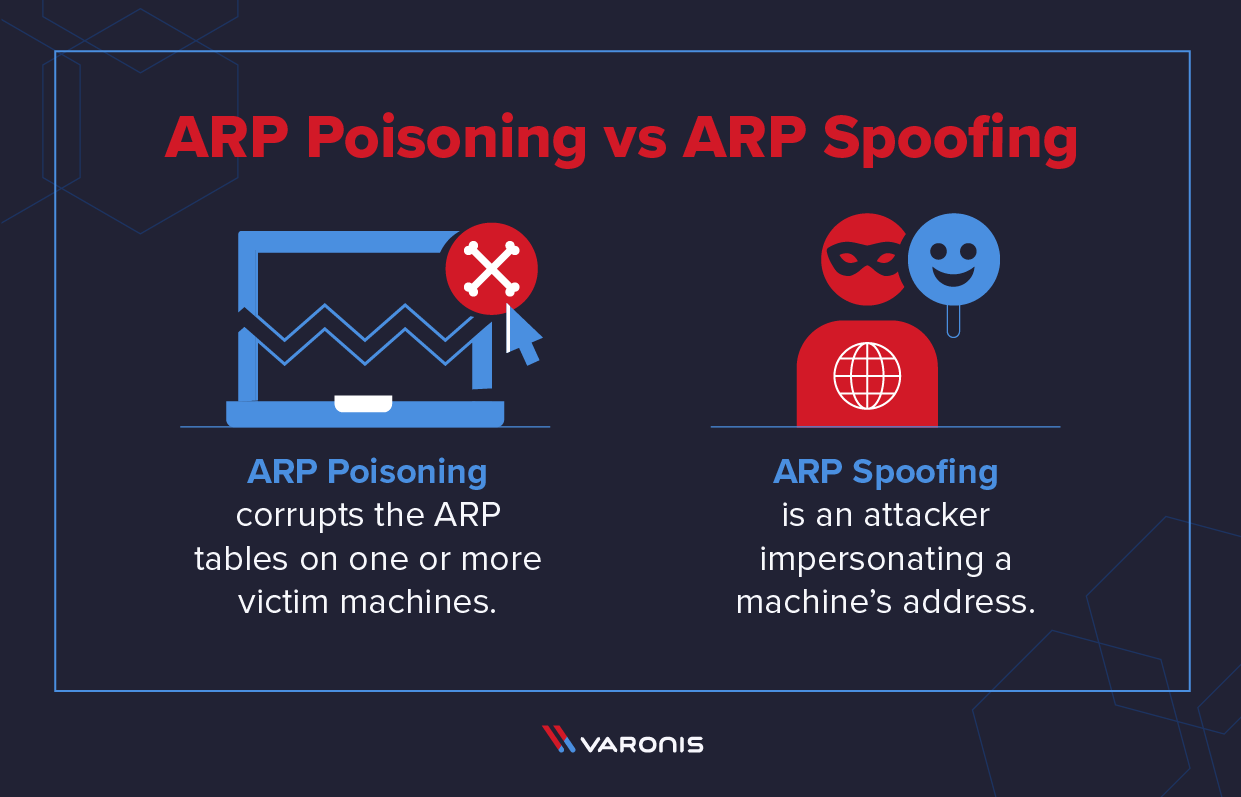
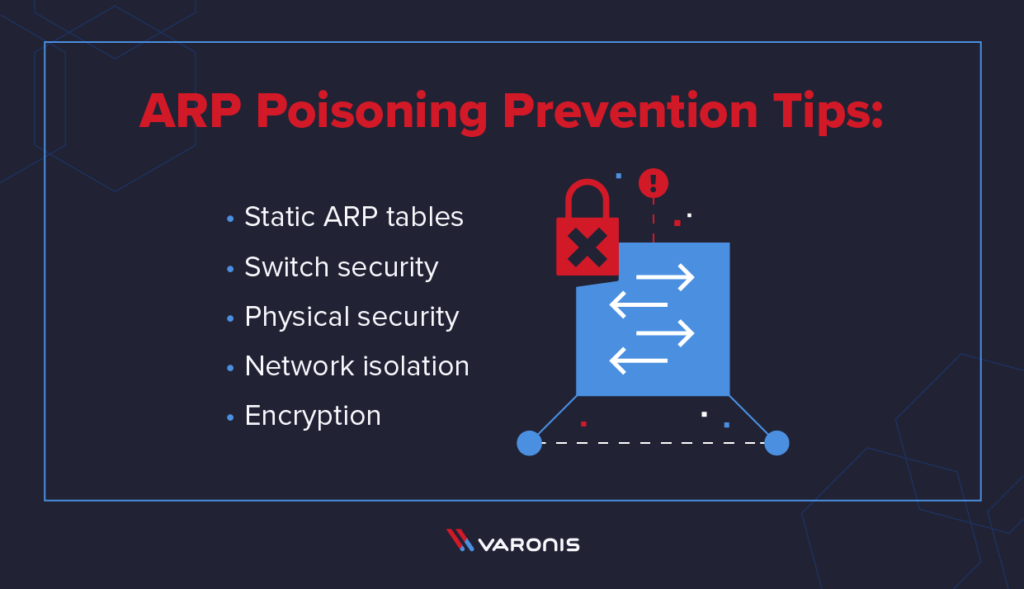
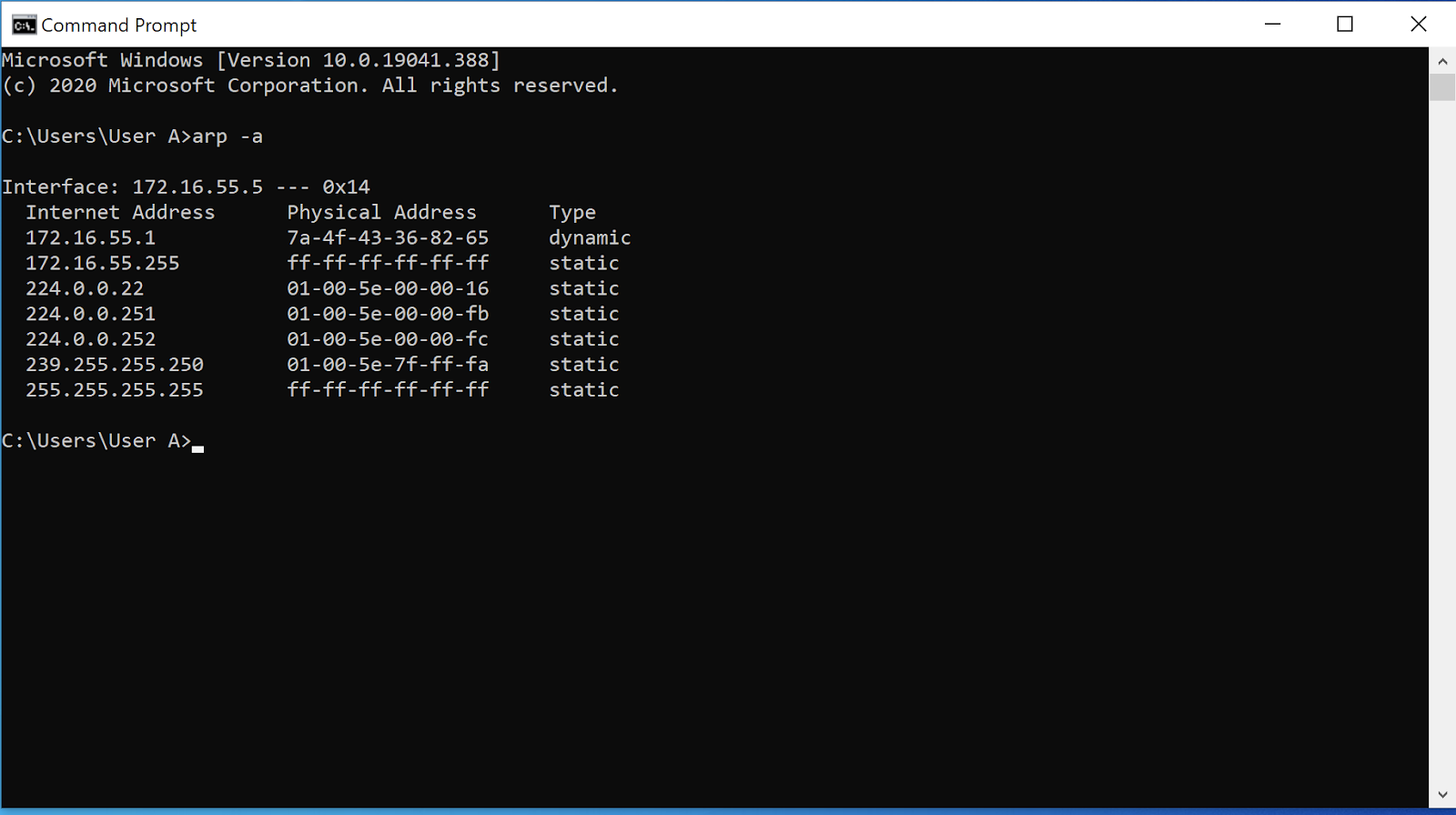
How To Prevent Arp Poisoning - One such technique is arp spoofing prevention, which involves configuring static arp entries on your devices to prevent. Prevention is key to mitigating the risks of arp poisoning. Fortunately, you can implement a number of procedures and tools as part of your incident response plan to prevent arp spoofing. Here are some effective strategies:
Fortunately, you can implement a number of procedures and tools as part of your incident response plan to prevent arp spoofing. Here are some effective strategies: Prevention is key to mitigating the risks of arp poisoning. One such technique is arp spoofing prevention, which involves configuring static arp entries on your devices to prevent.
One such technique is arp spoofing prevention, which involves configuring static arp entries on your devices to prevent. Prevention is key to mitigating the risks of arp poisoning. Fortunately, you can implement a number of procedures and tools as part of your incident response plan to prevent arp spoofing. Here are some effective strategies:
ARP Poisoning Attacks.ppt
Prevention is key to mitigating the risks of arp poisoning. Fortunately, you can implement a number of procedures and tools as part of your incident response plan to prevent arp spoofing. One such technique is arp spoofing prevention, which involves configuring static arp entries on your devices to prevent. Here are some effective strategies:
ARP Poisoning Attacks.ppt
Here are some effective strategies: One such technique is arp spoofing prevention, which involves configuring static arp entries on your devices to prevent. Prevention is key to mitigating the risks of arp poisoning. Fortunately, you can implement a number of procedures and tools as part of your incident response plan to prevent arp spoofing.
ARP poisoning Techniques, detection, and implications NordVPN
Fortunately, you can implement a number of procedures and tools as part of your incident response plan to prevent arp spoofing. Here are some effective strategies: One such technique is arp spoofing prevention, which involves configuring static arp entries on your devices to prevent. Prevention is key to mitigating the risks of arp poisoning.
ARP Poisoning What it is & How to Prevent ARP Spoofing Attacks
Here are some effective strategies: Fortunately, you can implement a number of procedures and tools as part of your incident response plan to prevent arp spoofing. One such technique is arp spoofing prevention, which involves configuring static arp entries on your devices to prevent. Prevention is key to mitigating the risks of arp poisoning.
ARP Poisoning What it is & How to Prevent ARP Spoofing Attacks
Prevention is key to mitigating the risks of arp poisoning. Here are some effective strategies: One such technique is arp spoofing prevention, which involves configuring static arp entries on your devices to prevent. Fortunately, you can implement a number of procedures and tools as part of your incident response plan to prevent arp spoofing.
Unit 4 ARP Poisoning PDF Ip Address I Pv6
Prevention is key to mitigating the risks of arp poisoning. Fortunately, you can implement a number of procedures and tools as part of your incident response plan to prevent arp spoofing. Here are some effective strategies: One such technique is arp spoofing prevention, which involves configuring static arp entries on your devices to prevent.
ARP Spoofing What is it and how can I protect myself?
Here are some effective strategies: Fortunately, you can implement a number of procedures and tools as part of your incident response plan to prevent arp spoofing. Prevention is key to mitigating the risks of arp poisoning. One such technique is arp spoofing prevention, which involves configuring static arp entries on your devices to prevent.
ARP Poisoning What it is & How to Prevent ARP Spoofing Attacks
Fortunately, you can implement a number of procedures and tools as part of your incident response plan to prevent arp spoofing. Prevention is key to mitigating the risks of arp poisoning. One such technique is arp spoofing prevention, which involves configuring static arp entries on your devices to prevent. Here are some effective strategies:
ARP Poisoning Attacks.ppt
Here are some effective strategies: Fortunately, you can implement a number of procedures and tools as part of your incident response plan to prevent arp spoofing. One such technique is arp spoofing prevention, which involves configuring static arp entries on your devices to prevent. Prevention is key to mitigating the risks of arp poisoning.
ARP spoofing on mobile How it works, risks and solutions
Here are some effective strategies: Fortunately, you can implement a number of procedures and tools as part of your incident response plan to prevent arp spoofing. One such technique is arp spoofing prevention, which involves configuring static arp entries on your devices to prevent. Prevention is key to mitigating the risks of arp poisoning.
Here Are Some Effective Strategies:
One such technique is arp spoofing prevention, which involves configuring static arp entries on your devices to prevent. Prevention is key to mitigating the risks of arp poisoning. Fortunately, you can implement a number of procedures and tools as part of your incident response plan to prevent arp spoofing.