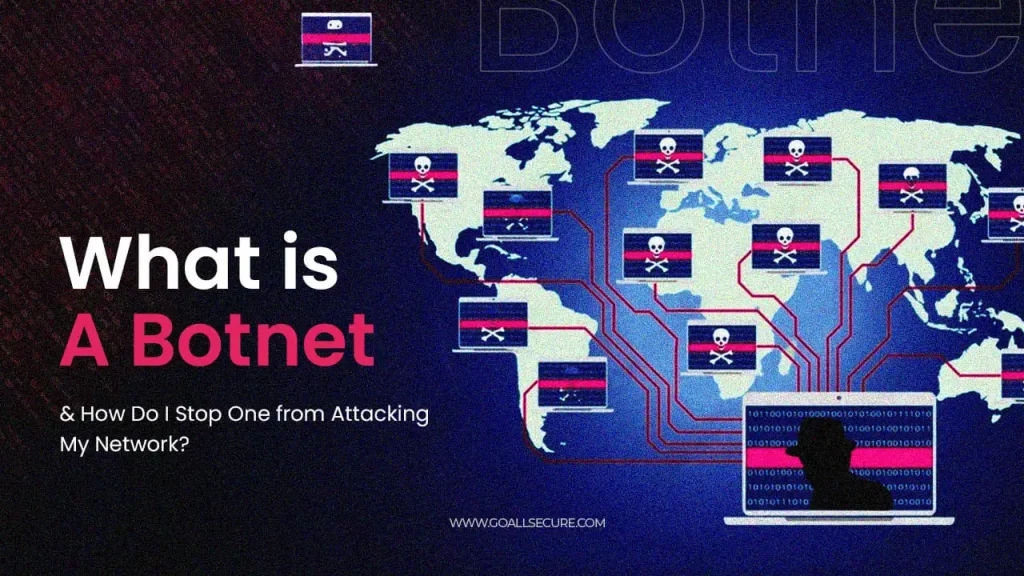
How To Prevent Botnet Attacks - As an individual or business, understanding what botnet attacks are and how to protect yourself is crucial for maintaining a. Botnet attacks use a command and control model to allow one or more hackers to drive the actions of those devices (often called ‘zombie bots’). The botnets are managed via irc to support unique.
Botnet attacks use a command and control model to allow one or more hackers to drive the actions of those devices (often called ‘zombie bots’). The botnets are managed via irc to support unique. As an individual or business, understanding what botnet attacks are and how to protect yourself is crucial for maintaining a.
The botnets are managed via irc to support unique. As an individual or business, understanding what botnet attacks are and how to protect yourself is crucial for maintaining a. Botnet attacks use a command and control model to allow one or more hackers to drive the actions of those devices (often called ‘zombie bots’).
How To Prevent Attacks On Your Network Tapscape
Botnet attacks use a command and control model to allow one or more hackers to drive the actions of those devices (often called ‘zombie bots’). The botnets are managed via irc to support unique. As an individual or business, understanding what botnet attacks are and how to protect yourself is crucial for maintaining a.
What Is a and How to Prevent Attacks in 2024?
Botnet attacks use a command and control model to allow one or more hackers to drive the actions of those devices (often called ‘zombie bots’). The botnets are managed via irc to support unique. As an individual or business, understanding what botnet attacks are and how to protect yourself is crucial for maintaining a.
How To Prevent Attacks On Your Network SecureBlitz
As an individual or business, understanding what botnet attacks are and how to protect yourself is crucial for maintaining a. Botnet attacks use a command and control model to allow one or more hackers to drive the actions of those devices (often called ‘zombie bots’). The botnets are managed via irc to support unique.
Attacks & Prevention Tips 2019 CYBERVIE
Botnet attacks use a command and control model to allow one or more hackers to drive the actions of those devices (often called ‘zombie bots’). As an individual or business, understanding what botnet attacks are and how to protect yourself is crucial for maintaining a. The botnets are managed via irc to support unique.
What Are IoT Attacks and How Can You Prevent Them?
Botnet attacks use a command and control model to allow one or more hackers to drive the actions of those devices (often called ‘zombie bots’). The botnets are managed via irc to support unique. As an individual or business, understanding what botnet attacks are and how to protect yourself is crucial for maintaining a.
Attacks & Prevention Tips 2019 CYBERVIE
The botnets are managed via irc to support unique. As an individual or business, understanding what botnet attacks are and how to protect yourself is crucial for maintaining a. Botnet attacks use a command and control model to allow one or more hackers to drive the actions of those devices (often called ‘zombie bots’).
Revealing Insights on How to Prevent Attacks in 2023
Botnet attacks use a command and control model to allow one or more hackers to drive the actions of those devices (often called ‘zombie bots’). The botnets are managed via irc to support unique. As an individual or business, understanding what botnet attacks are and how to protect yourself is crucial for maintaining a.
Revealing Insights on How to Prevent Attacks in 2023
The botnets are managed via irc to support unique. Botnet attacks use a command and control model to allow one or more hackers to drive the actions of those devices (often called ‘zombie bots’). As an individual or business, understanding what botnet attacks are and how to protect yourself is crucial for maintaining a.
Infographic Is Your Computer a Zombie? OPSWAT
As an individual or business, understanding what botnet attacks are and how to protect yourself is crucial for maintaining a. The botnets are managed via irc to support unique. Botnet attacks use a command and control model to allow one or more hackers to drive the actions of those devices (often called ‘zombie bots’).
Wallpapers Wallpaper Cave
Botnet attacks use a command and control model to allow one or more hackers to drive the actions of those devices (often called ‘zombie bots’). The botnets are managed via irc to support unique. As an individual or business, understanding what botnet attacks are and how to protect yourself is crucial for maintaining a.
As An Individual Or Business, Understanding What Botnet Attacks Are And How To Protect Yourself Is Crucial For Maintaining A.
Botnet attacks use a command and control model to allow one or more hackers to drive the actions of those devices (often called ‘zombie bots’). The botnets are managed via irc to support unique.