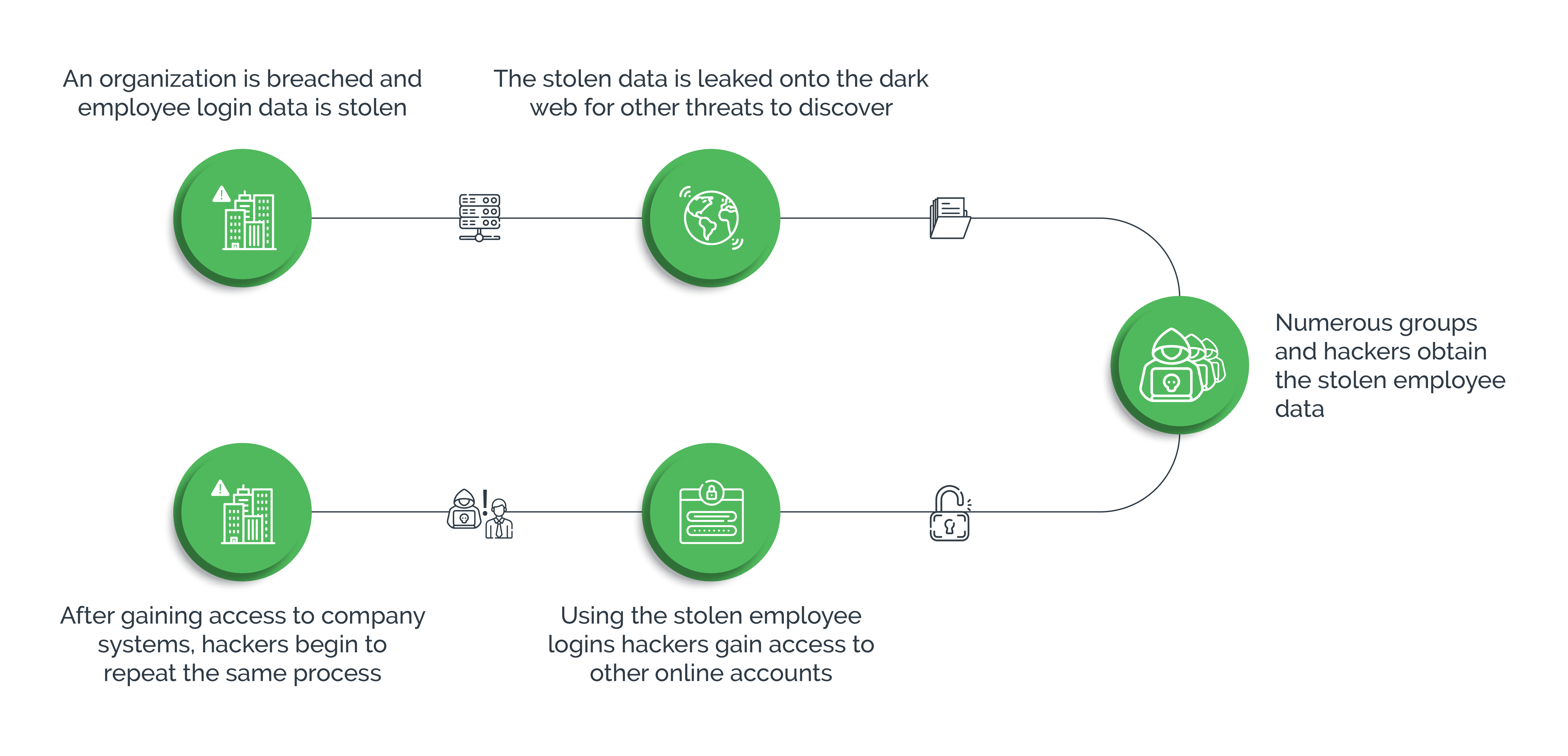
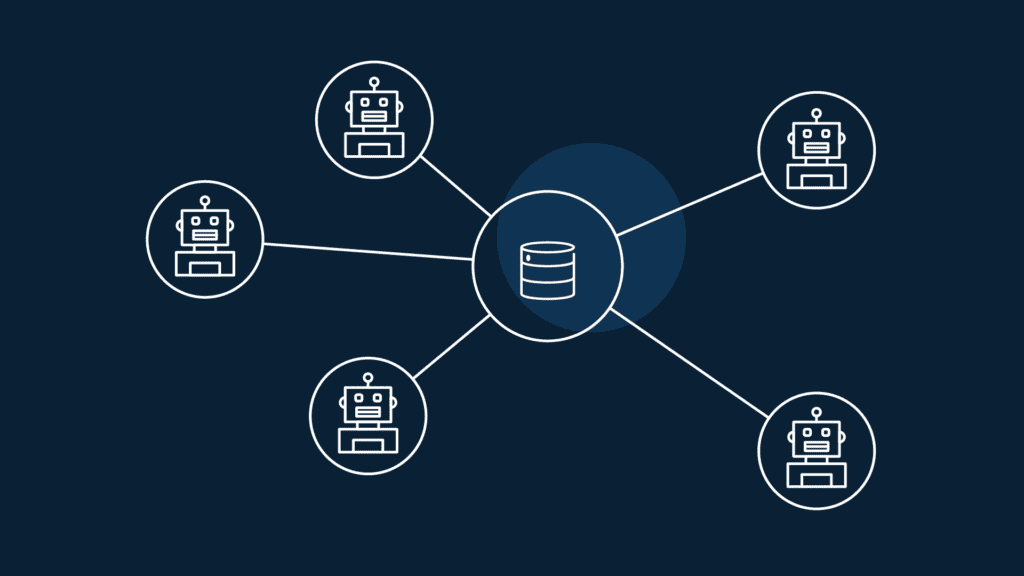
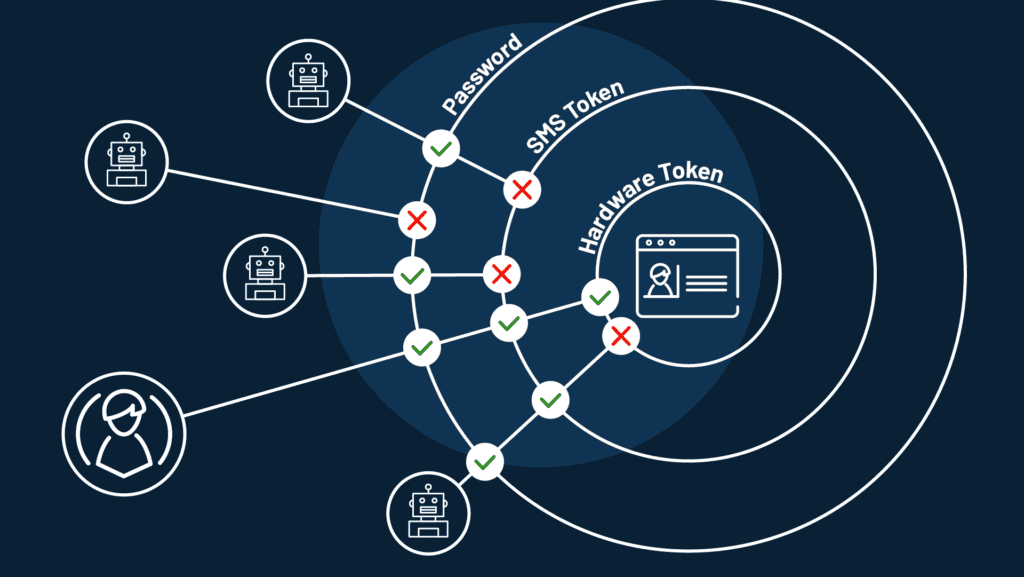
How To Prevent Credential Stuffing Attack - In this article, we’ll explore the risks of credential stuffing attacks, common techniques used by attackers, signs that your accounts. While you can’t completely prevent your login details from being stolen in a wider data breach, you can use the tips above to help.
In this article, we’ll explore the risks of credential stuffing attacks, common techniques used by attackers, signs that your accounts. While you can’t completely prevent your login details from being stolen in a wider data breach, you can use the tips above to help.
In this article, we’ll explore the risks of credential stuffing attacks, common techniques used by attackers, signs that your accounts. While you can’t completely prevent your login details from being stolen in a wider data breach, you can use the tips above to help.
What is a credential stuffing attack? Examples & Mitigation
In this article, we’ll explore the risks of credential stuffing attacks, common techniques used by attackers, signs that your accounts. While you can’t completely prevent your login details from being stolen in a wider data breach, you can use the tips above to help.
HOW TO PREVENT CREDENTIAL STUFFING ATTACK Finance Derivative
While you can’t completely prevent your login details from being stolen in a wider data breach, you can use the tips above to help. In this article, we’ll explore the risks of credential stuffing attacks, common techniques used by attackers, signs that your accounts.
How to Prevent Credential Stuffing Attacks Arkose Labs
While you can’t completely prevent your login details from being stolen in a wider data breach, you can use the tips above to help. In this article, we’ll explore the risks of credential stuffing attacks, common techniques used by attackers, signs that your accounts.
Credential Stuffing Attack on PayPal Accounts & How MTE Technology
In this article, we’ll explore the risks of credential stuffing attacks, common techniques used by attackers, signs that your accounts. While you can’t completely prevent your login details from being stolen in a wider data breach, you can use the tips above to help.
Credential Stuffing Attack Explained and Prevent In NewsWeekly
While you can’t completely prevent your login details from being stolen in a wider data breach, you can use the tips above to help. In this article, we’ll explore the risks of credential stuffing attacks, common techniques used by attackers, signs that your accounts.
Credential Stuffing How To Detect And Prevent It
While you can’t completely prevent your login details from being stolen in a wider data breach, you can use the tips above to help. In this article, we’ll explore the risks of credential stuffing attacks, common techniques used by attackers, signs that your accounts.
Credential Stuffing How To Detect And Prevent It
While you can’t completely prevent your login details from being stolen in a wider data breach, you can use the tips above to help. In this article, we’ll explore the risks of credential stuffing attacks, common techniques used by attackers, signs that your accounts.
Credential Stuffing How To Detect And Prevent It LoginRadius
In this article, we’ll explore the risks of credential stuffing attacks, common techniques used by attackers, signs that your accounts. While you can’t completely prevent your login details from being stolen in a wider data breach, you can use the tips above to help.
What is a Credential Stuffing Attack
While you can’t completely prevent your login details from being stolen in a wider data breach, you can use the tips above to help. In this article, we’ll explore the risks of credential stuffing attacks, common techniques used by attackers, signs that your accounts.
What is a Credential Stuffing Attack and How to Prevent Them
While you can’t completely prevent your login details from being stolen in a wider data breach, you can use the tips above to help. In this article, we’ll explore the risks of credential stuffing attacks, common techniques used by attackers, signs that your accounts.
While You Can’t Completely Prevent Your Login Details From Being Stolen In A Wider Data Breach, You Can Use The Tips Above To Help.
In this article, we’ll explore the risks of credential stuffing attacks, common techniques used by attackers, signs that your accounts.