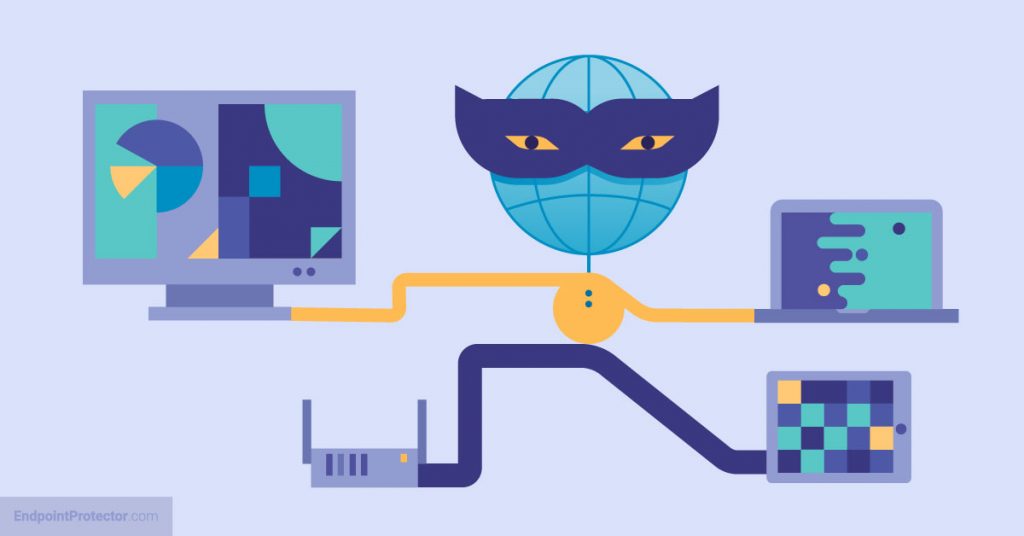
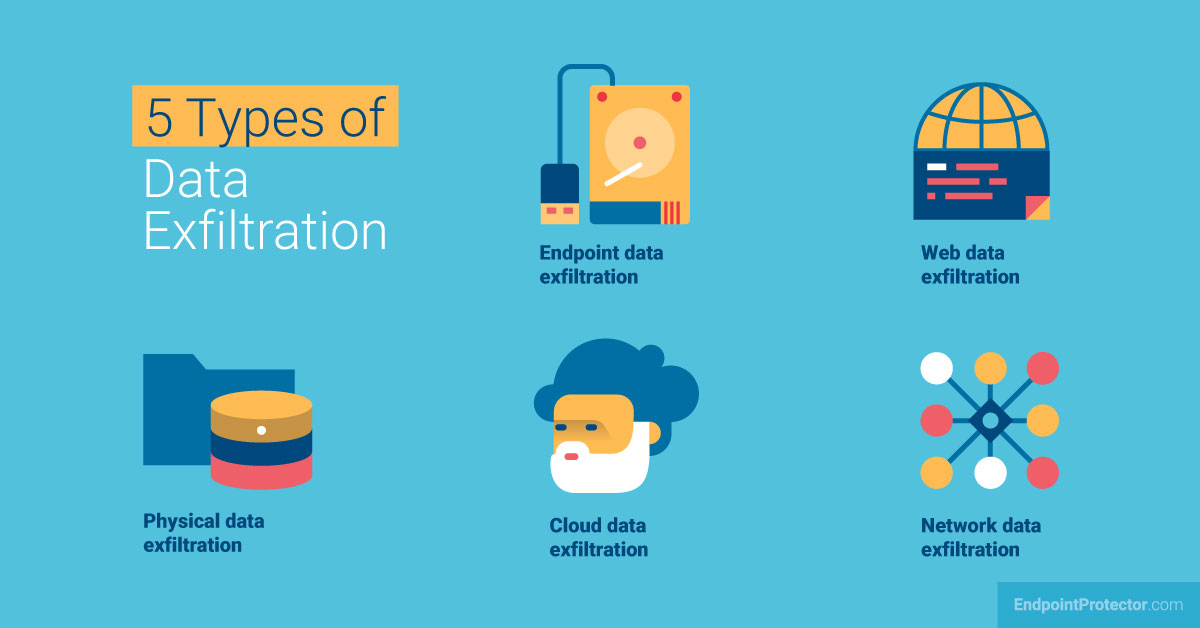
How To Prevent Data Exfiltration - While data leaks are the accidental exposure of sensitive information to unapproved parties, data exfiltration is the deliberate act of. Discover the key methods of data exfiltration, its impact on businesses, and effective strategies for prevention.
Discover the key methods of data exfiltration, its impact on businesses, and effective strategies for prevention. While data leaks are the accidental exposure of sensitive information to unapproved parties, data exfiltration is the deliberate act of.
Discover the key methods of data exfiltration, its impact on businesses, and effective strategies for prevention. While data leaks are the accidental exposure of sensitive information to unapproved parties, data exfiltration is the deliberate act of.
Prevent Data Exfiltration The Complete Guide Endpoint Protector
While data leaks are the accidental exposure of sensitive information to unapproved parties, data exfiltration is the deliberate act of. Discover the key methods of data exfiltration, its impact on businesses, and effective strategies for prevention.
Prevent Data Exfiltration The Complete Guide Endpoint Protector
Discover the key methods of data exfiltration, its impact on businesses, and effective strategies for prevention. While data leaks are the accidental exposure of sensitive information to unapproved parties, data exfiltration is the deliberate act of.
Data Exfiltration Meaning, Examples & How to Prevent It Ekran System
While data leaks are the accidental exposure of sensitive information to unapproved parties, data exfiltration is the deliberate act of. Discover the key methods of data exfiltration, its impact on businesses, and effective strategies for prevention.
Prevent Data Exfiltration The Complete Guide Endpoint Protector
Discover the key methods of data exfiltration, its impact on businesses, and effective strategies for prevention. While data leaks are the accidental exposure of sensitive information to unapproved parties, data exfiltration is the deliberate act of.
Data Exfiltration Methodology PDF Ip Address Port
Discover the key methods of data exfiltration, its impact on businesses, and effective strategies for prevention. While data leaks are the accidental exposure of sensitive information to unapproved parties, data exfiltration is the deliberate act of.
Data Exfiltration How to prevent it GreenCloud Affordable KVM and
Discover the key methods of data exfiltration, its impact on businesses, and effective strategies for prevention. While data leaks are the accidental exposure of sensitive information to unapproved parties, data exfiltration is the deliberate act of.
Shielding Your Sensitive Data Preventing Data Exfiltration
While data leaks are the accidental exposure of sensitive information to unapproved parties, data exfiltration is the deliberate act of. Discover the key methods of data exfiltration, its impact on businesses, and effective strategies for prevention.
Threat Insight Prevent Data Exfiltration via DNS Video Infoblox
Discover the key methods of data exfiltration, its impact on businesses, and effective strategies for prevention. While data leaks are the accidental exposure of sensitive information to unapproved parties, data exfiltration is the deliberate act of.
Data Exfiltration Meaning, Examples & How to Prevent It Ekran System
Discover the key methods of data exfiltration, its impact on businesses, and effective strategies for prevention. While data leaks are the accidental exposure of sensitive information to unapproved parties, data exfiltration is the deliberate act of.
While Data Leaks Are The Accidental Exposure Of Sensitive Information To Unapproved Parties, Data Exfiltration Is The Deliberate Act Of.
Discover the key methods of data exfiltration, its impact on businesses, and effective strategies for prevention.