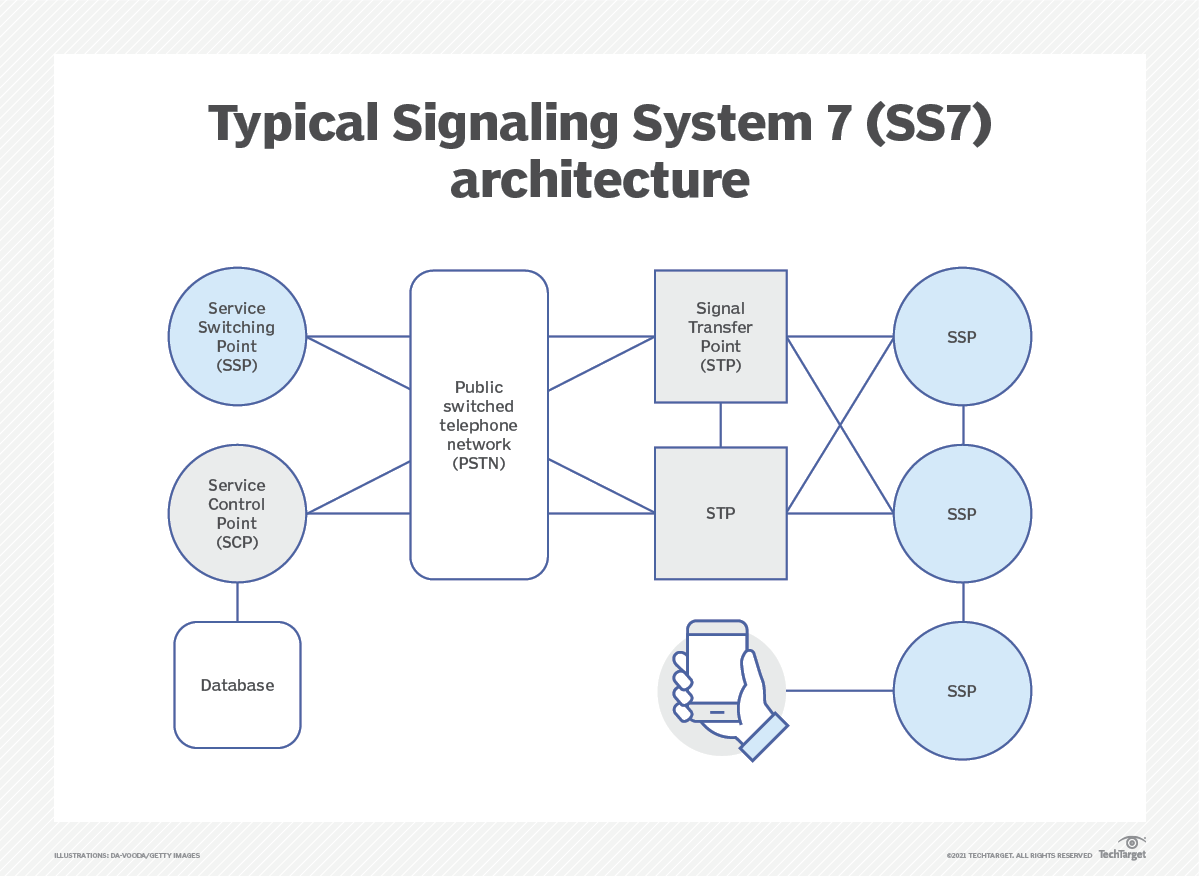
How To Prevent Ss7 Attack - To conduct an ss7 attack, a cybercriminal requires a computer running linux and the ss7. In recent years, attackers have leveraged ss7 vulnerabilities to intercept calls and text.
To conduct an ss7 attack, a cybercriminal requires a computer running linux and the ss7. In recent years, attackers have leveraged ss7 vulnerabilities to intercept calls and text.
To conduct an ss7 attack, a cybercriminal requires a computer running linux and the ss7. In recent years, attackers have leveraged ss7 vulnerabilities to intercept calls and text.
SS7 Locate Track Manipulate Attack SPY24
To conduct an ss7 attack, a cybercriminal requires a computer running linux and the ss7. In recent years, attackers have leveraged ss7 vulnerabilities to intercept calls and text.
SS7 Attack What Is It, How SS7 Attack Works, and Prevention Techniques
In recent years, attackers have leveraged ss7 vulnerabilities to intercept calls and text. To conduct an ss7 attack, a cybercriminal requires a computer running linux and the ss7.
SS7 Attack What Is It, How SS7 Attack Works, and Prevention Techniques
In recent years, attackers have leveraged ss7 vulnerabilities to intercept calls and text. To conduct an ss7 attack, a cybercriminal requires a computer running linux and the ss7.
GitHub mopster81/SS7Attack knowledge about SS7 attack and hack
In recent years, attackers have leveraged ss7 vulnerabilities to intercept calls and text. To conduct an ss7 attack, a cybercriminal requires a computer running linux and the ss7.
SS7 Attack What Is It, How SS7 Attack Works, and Prevention Techniques
In recent years, attackers have leveraged ss7 vulnerabilities to intercept calls and text. To conduct an ss7 attack, a cybercriminal requires a computer running linux and the ss7.
SS7 Attack What Is It, How SS7 Attack Works, and Prevention Techniques
To conduct an ss7 attack, a cybercriminal requires a computer running linux and the ss7. In recent years, attackers have leveraged ss7 vulnerabilities to intercept calls and text.
GitHub PenteSploit/ss7attack
To conduct an ss7 attack, a cybercriminal requires a computer running linux and the ss7. In recent years, attackers have leveraged ss7 vulnerabilities to intercept calls and text.
SS7 Attack What Is It, How SS7 Attack Works, and Prevention Techniques
To conduct an ss7 attack, a cybercriminal requires a computer running linux and the ss7. In recent years, attackers have leveraged ss7 vulnerabilities to intercept calls and text.
GitHub polarking/jss7attacksimulator SS7 Attack Simulator based on
To conduct an ss7 attack, a cybercriminal requires a computer running linux and the ss7. In recent years, attackers have leveraged ss7 vulnerabilities to intercept calls and text.
In Recent Years, Attackers Have Leveraged Ss7 Vulnerabilities To Intercept Calls And Text.
To conduct an ss7 attack, a cybercriminal requires a computer running linux and the ss7.