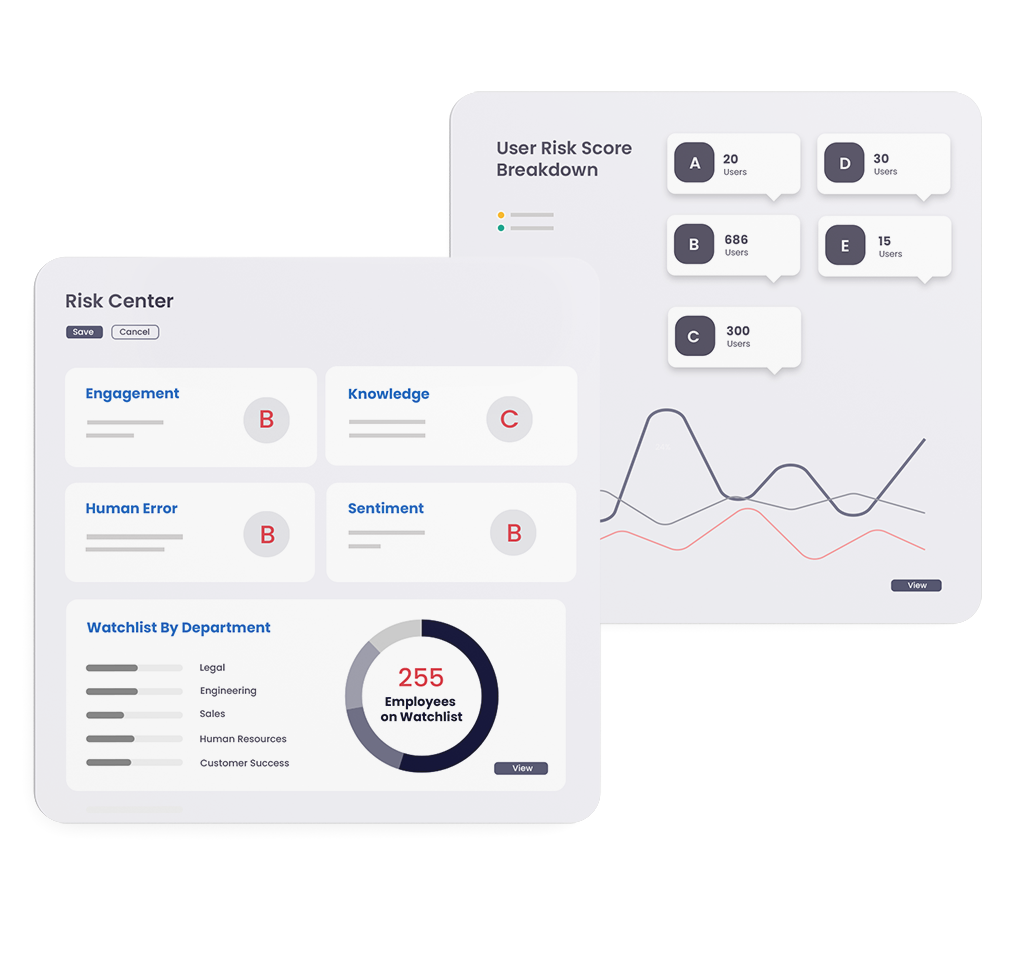
Mimecast Data Leak Prevention - This guide describes how to monitor data leak prevention by accessing log. A series of mimecast policies can be used in the prevention of data leakage.
A series of mimecast policies can be used in the prevention of data leakage. This guide describes how to monitor data leak prevention by accessing log.
This guide describes how to monitor data leak prevention by accessing log. A series of mimecast policies can be used in the prevention of data leakage.
Data Leakage Prevention Solutions Mimecast
This guide describes how to monitor data leak prevention by accessing log. A series of mimecast policies can be used in the prevention of data leakage.
What is Data Leakage Prevention Data Leak Protection (DLP) Mimecast
This guide describes how to monitor data leak prevention by accessing log. A series of mimecast policies can be used in the prevention of data leakage.
All Articles Mimecast Blog Mimecast
This guide describes how to monitor data leak prevention by accessing log. A series of mimecast policies can be used in the prevention of data leakage.
What is Data Leakage Prevention Data Leak Protection (DLP) Mimecast
A series of mimecast policies can be used in the prevention of data leakage. This guide describes how to monitor data leak prevention by accessing log.
Data Loss Prevention Software Mimecast
A series of mimecast policies can be used in the prevention of data leakage. This guide describes how to monitor data leak prevention by accessing log.
What is Data Loss Prevention (DLP) Mimecast
This guide describes how to monitor data leak prevention by accessing log. A series of mimecast policies can be used in the prevention of data leakage.
Email Security, Archiving and Continuity Products Mimecast
A series of mimecast policies can be used in the prevention of data leakage. This guide describes how to monitor data leak prevention by accessing log.
Email & Collaboration Security Mimecast
This guide describes how to monitor data leak prevention by accessing log. A series of mimecast policies can be used in the prevention of data leakage.
Data Leak Prevention Services Technical Framework
This guide describes how to monitor data leak prevention by accessing log. A series of mimecast policies can be used in the prevention of data leakage.
A Series Of Mimecast Policies Can Be Used In The Prevention Of Data Leakage.
This guide describes how to monitor data leak prevention by accessing log.