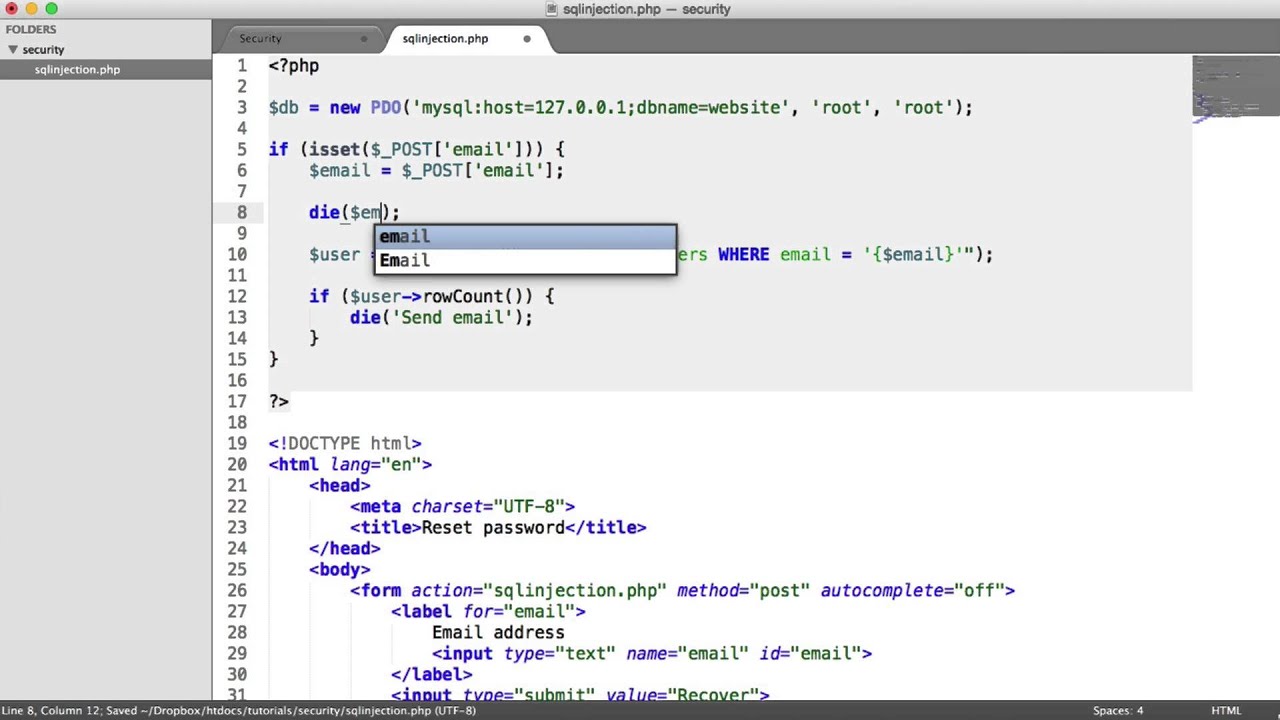
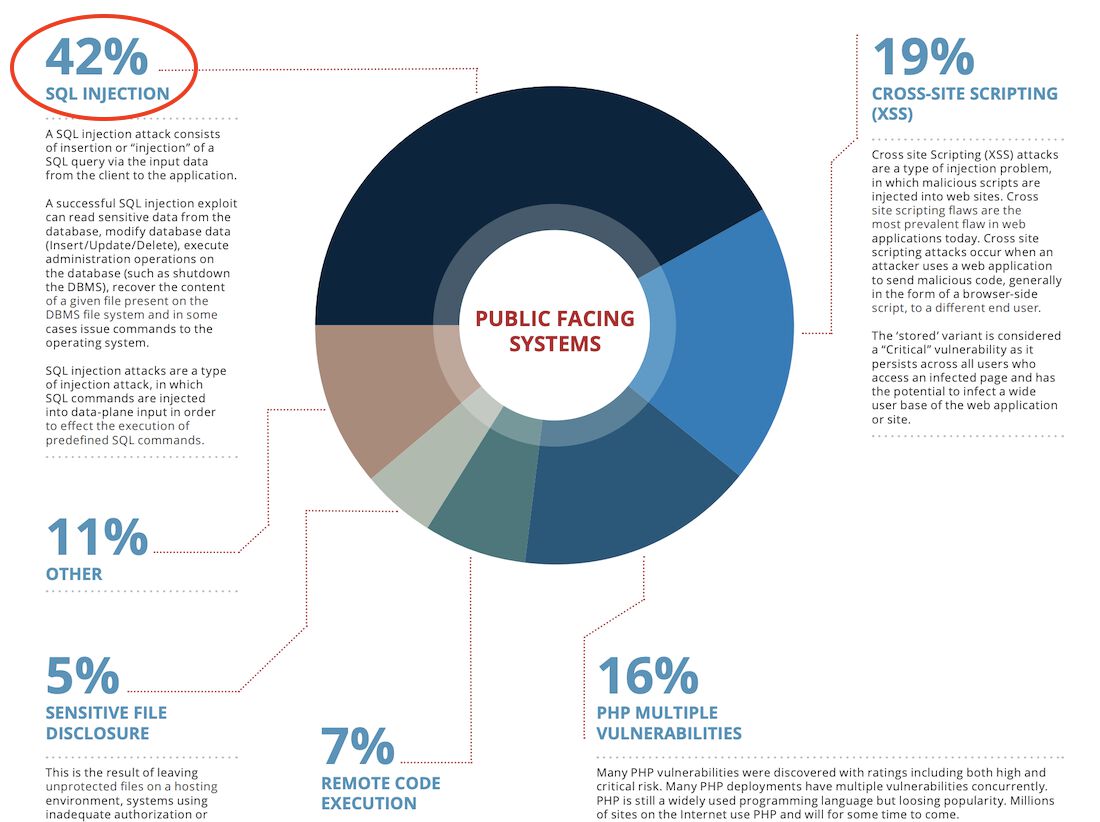
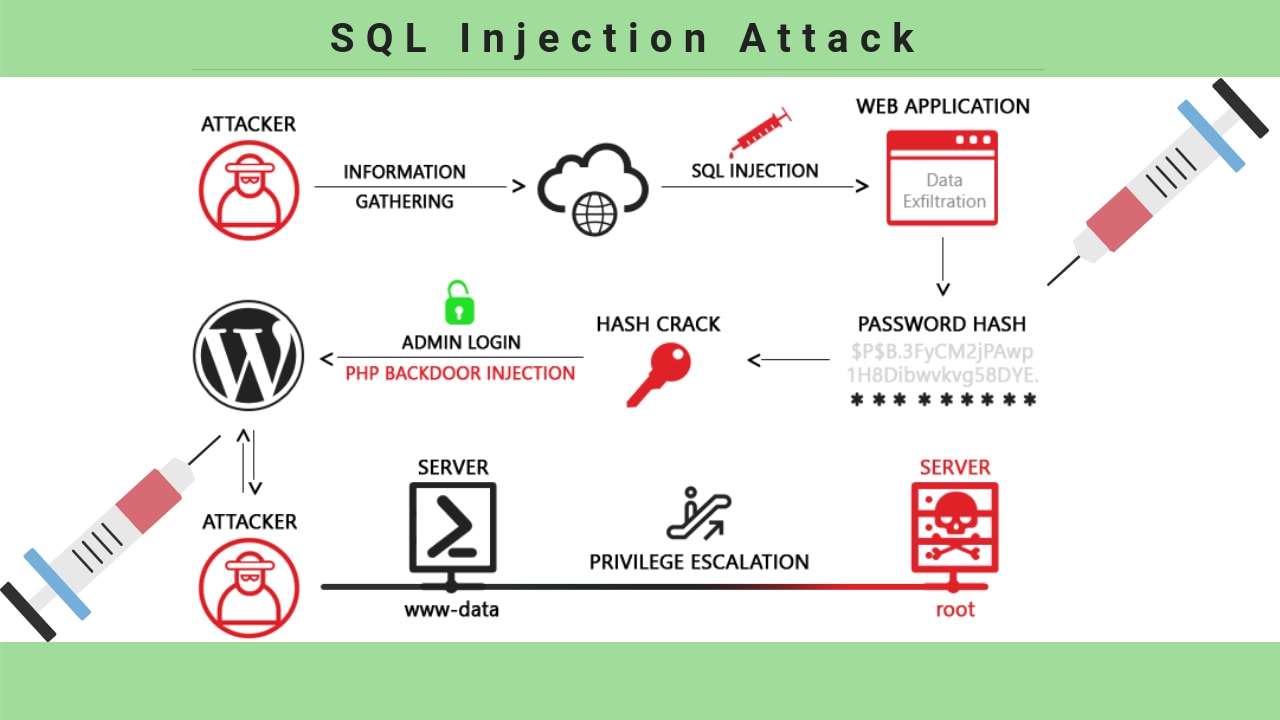
Php Function To Prevent Sql Injection - In this tutorial, we’ll discuss best practices and strategies to prevent sql injection attacks in php programs, showcasing the. Prepared statements are the most effective way to prevent sql injection. The correct way to avoid sql injection attacks, no matter which database you use, is to separate the data from sql, so that. They separate sql code from user data, ensuring.
They separate sql code from user data, ensuring. In this tutorial, we’ll discuss best practices and strategies to prevent sql injection attacks in php programs, showcasing the. Prepared statements are the most effective way to prevent sql injection. The correct way to avoid sql injection attacks, no matter which database you use, is to separate the data from sql, so that.
Prepared statements are the most effective way to prevent sql injection. They separate sql code from user data, ensuring. In this tutorial, we’ll discuss best practices and strategies to prevent sql injection attacks in php programs, showcasing the. The correct way to avoid sql injection attacks, no matter which database you use, is to separate the data from sql, so that.
How to Prevent SQL Injection in PHP (with Pictures) wikiHow
They separate sql code from user data, ensuring. The correct way to avoid sql injection attacks, no matter which database you use, is to separate the data from sql, so that. Prepared statements are the most effective way to prevent sql injection. In this tutorial, we’ll discuss best practices and strategies to prevent sql injection attacks in php programs, showcasing.
How to Prevent SQL Injection in PHP A Comprehensive Guide Laravelicious
In this tutorial, we’ll discuss best practices and strategies to prevent sql injection attacks in php programs, showcasing the. They separate sql code from user data, ensuring. The correct way to avoid sql injection attacks, no matter which database you use, is to separate the data from sql, so that. Prepared statements are the most effective way to prevent sql.
How To Prevent Sql Injection In Php Crazyscreen21
The correct way to avoid sql injection attacks, no matter which database you use, is to separate the data from sql, so that. Prepared statements are the most effective way to prevent sql injection. They separate sql code from user data, ensuring. In this tutorial, we’ll discuss best practices and strategies to prevent sql injection attacks in php programs, showcasing.
Amazing Info About How To Prevent Sql Injection Php Fishreward32
The correct way to avoid sql injection attacks, no matter which database you use, is to separate the data from sql, so that. They separate sql code from user data, ensuring. In this tutorial, we’ll discuss best practices and strategies to prevent sql injection attacks in php programs, showcasing the. Prepared statements are the most effective way to prevent sql.
How to Prevent SQL Injection in PHP (with Pictures) wikiHow
They separate sql code from user data, ensuring. The correct way to avoid sql injection attacks, no matter which database you use, is to separate the data from sql, so that. Prepared statements are the most effective way to prevent sql injection. In this tutorial, we’ll discuss best practices and strategies to prevent sql injection attacks in php programs, showcasing.
How to Prevent SQL Injection in PHP (with Pictures) wikiHow
In this tutorial, we’ll discuss best practices and strategies to prevent sql injection attacks in php programs, showcasing the. The correct way to avoid sql injection attacks, no matter which database you use, is to separate the data from sql, so that. They separate sql code from user data, ensuring. Prepared statements are the most effective way to prevent sql.
Prevent SQL Injection in PHP Phppot
They separate sql code from user data, ensuring. In this tutorial, we’ll discuss best practices and strategies to prevent sql injection attacks in php programs, showcasing the. The correct way to avoid sql injection attacks, no matter which database you use, is to separate the data from sql, so that. Prepared statements are the most effective way to prevent sql.
Amazing Info About How To Prevent Sql Injection Php Fishreward32
The correct way to avoid sql injection attacks, no matter which database you use, is to separate the data from sql, so that. They separate sql code from user data, ensuring. In this tutorial, we’ll discuss best practices and strategies to prevent sql injection attacks in php programs, showcasing the. Prepared statements are the most effective way to prevent sql.
How to prevent SQL injection in PHP?
Prepared statements are the most effective way to prevent sql injection. They separate sql code from user data, ensuring. In this tutorial, we’ll discuss best practices and strategies to prevent sql injection attacks in php programs, showcasing the. The correct way to avoid sql injection attacks, no matter which database you use, is to separate the data from sql, so.
3 Ways to Prevent SQL Injection in PHP wikiHow
The correct way to avoid sql injection attacks, no matter which database you use, is to separate the data from sql, so that. They separate sql code from user data, ensuring. Prepared statements are the most effective way to prevent sql injection. In this tutorial, we’ll discuss best practices and strategies to prevent sql injection attacks in php programs, showcasing.
In This Tutorial, We’ll Discuss Best Practices And Strategies To Prevent Sql Injection Attacks In Php Programs, Showcasing The.
They separate sql code from user data, ensuring. Prepared statements are the most effective way to prevent sql injection. The correct way to avoid sql injection attacks, no matter which database you use, is to separate the data from sql, so that.