Prevent Detect Respond - Ensure risk responses are identified and prioritized, executed, and results monitored. Develop and implement the appropriate. Learn how the detect function defines the appropriate activities to identify the occurrence of a cybersecurity event. The csf 2.0 is organized by six functions — govern, identify, protect, detect, respond, and recover. Govern, identify, and protect outcomes help prevent and prepare for incidents, while govern, detect, respond, and recover outcomes. Together, these functions provide a. Detect and analyse cyber security events to identify cyber security incidents.
The csf 2.0 is organized by six functions — govern, identify, protect, detect, respond, and recover. Govern, identify, and protect outcomes help prevent and prepare for incidents, while govern, detect, respond, and recover outcomes. Learn how the detect function defines the appropriate activities to identify the occurrence of a cybersecurity event. Detect and analyse cyber security events to identify cyber security incidents. Ensure risk responses are identified and prioritized, executed, and results monitored. Together, these functions provide a. Develop and implement the appropriate.
Ensure risk responses are identified and prioritized, executed, and results monitored. Develop and implement the appropriate. Together, these functions provide a. Learn how the detect function defines the appropriate activities to identify the occurrence of a cybersecurity event. Detect and analyse cyber security events to identify cyber security incidents. The csf 2.0 is organized by six functions — govern, identify, protect, detect, respond, and recover. Govern, identify, and protect outcomes help prevent and prepare for incidents, while govern, detect, respond, and recover outcomes.
Things to help you Identify, Prevent, Detect, and Respond to Cyber
Learn how the detect function defines the appropriate activities to identify the occurrence of a cybersecurity event. Govern, identify, and protect outcomes help prevent and prepare for incidents, while govern, detect, respond, and recover outcomes. Develop and implement the appropriate. Ensure risk responses are identified and prioritized, executed, and results monitored. The csf 2.0 is organized by six functions —.
Predict, Prevent, Detect and Respond 8 Tips to Secure Your Business
The csf 2.0 is organized by six functions — govern, identify, protect, detect, respond, and recover. Develop and implement the appropriate. Together, these functions provide a. Ensure risk responses are identified and prioritized, executed, and results monitored. Detect and analyse cyber security events to identify cyber security incidents.
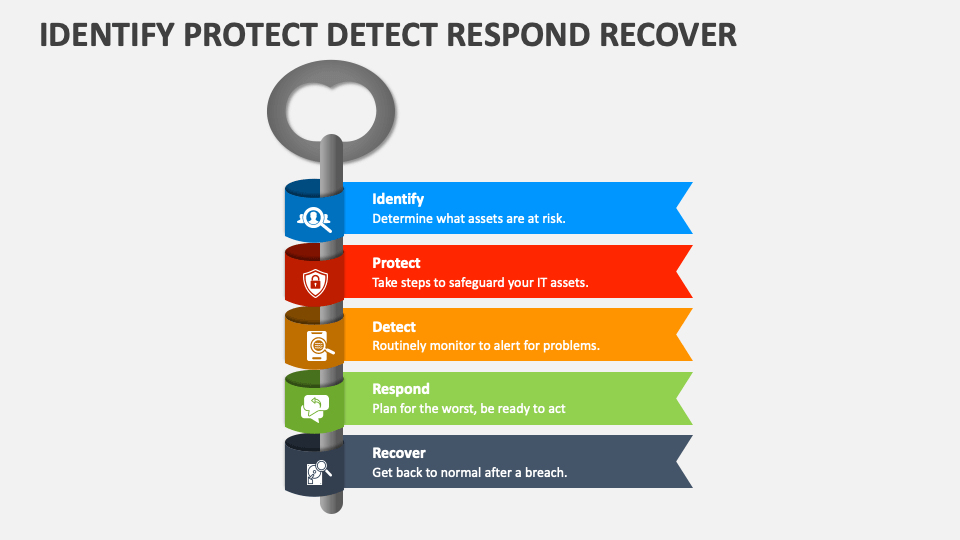
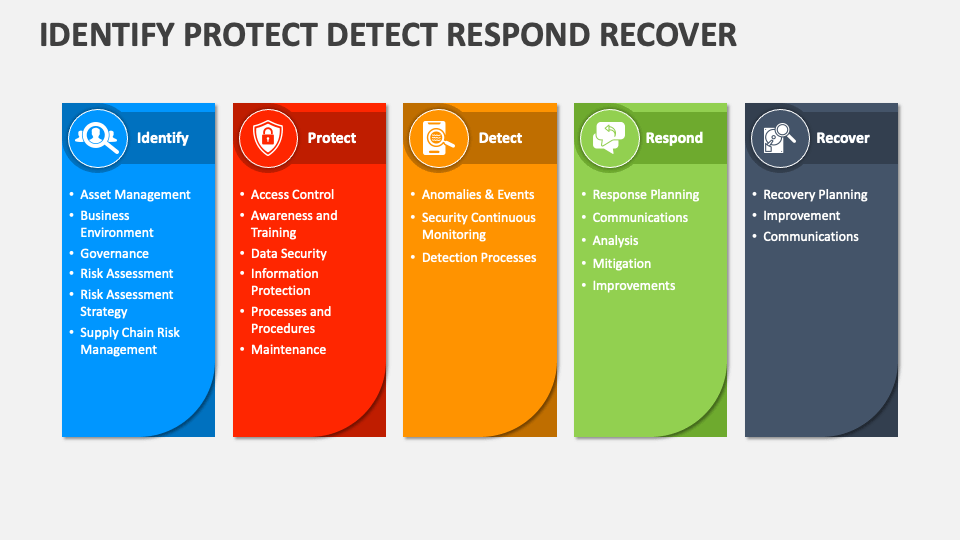
Identify Protect Detect Respond Recover PowerPoint Presentation Slides
Develop and implement the appropriate. Learn how the detect function defines the appropriate activities to identify the occurrence of a cybersecurity event. Together, these functions provide a. Detect and analyse cyber security events to identify cyber security incidents. Govern, identify, and protect outcomes help prevent and prepare for incidents, while govern, detect, respond, and recover outcomes.
The PreventDetectRecover Cycle Cloud Gal 42
The csf 2.0 is organized by six functions — govern, identify, protect, detect, respond, and recover. Ensure risk responses are identified and prioritized, executed, and results monitored. Together, these functions provide a. Govern, identify, and protect outcomes help prevent and prepare for incidents, while govern, detect, respond, and recover outcomes. Learn how the detect function defines the appropriate activities to.
Identify Protect Detect Respond Recover Business powerpoint templates
Detect and analyse cyber security events to identify cyber security incidents. Develop and implement the appropriate. The csf 2.0 is organized by six functions — govern, identify, protect, detect, respond, and recover. Ensure risk responses are identified and prioritized, executed, and results monitored. Learn how the detect function defines the appropriate activities to identify the occurrence of a cybersecurity event.
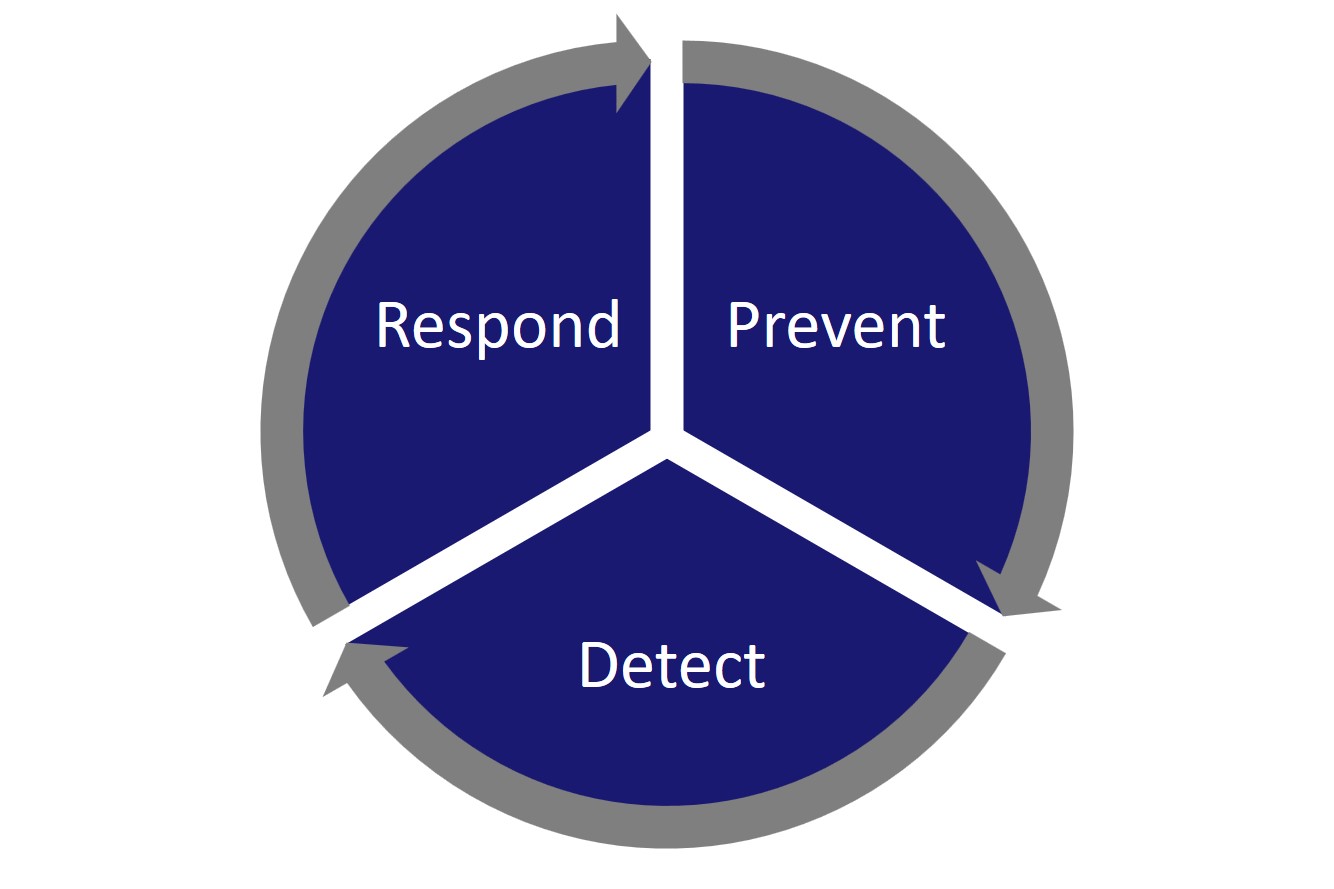
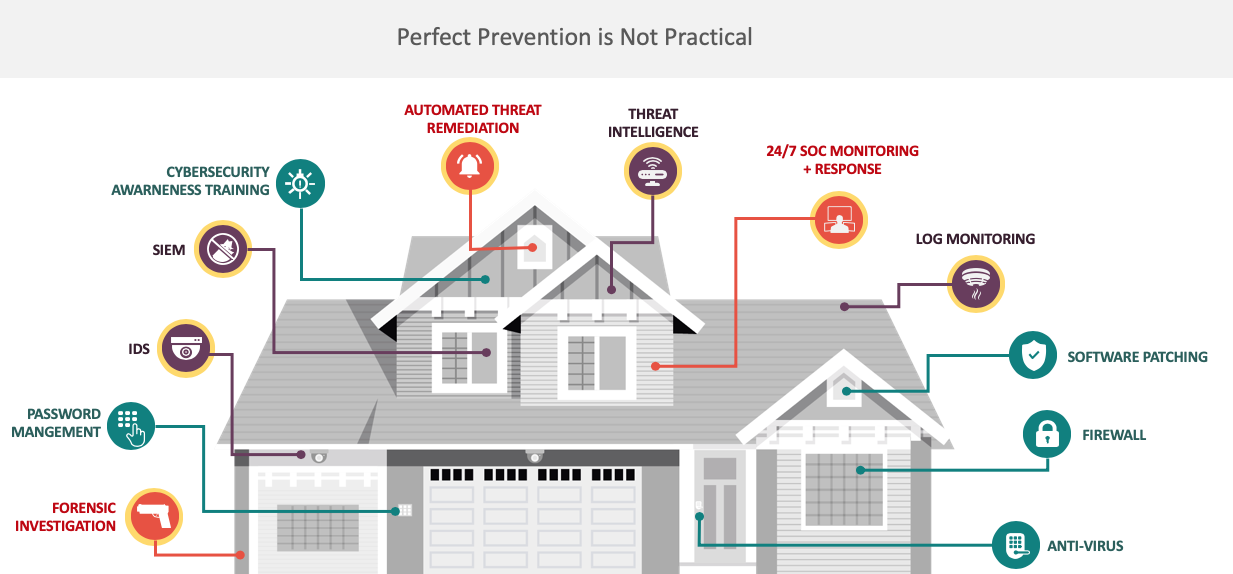
Prevent, Detect & Respond ICS
Detect and analyse cyber security events to identify cyber security incidents. The csf 2.0 is organized by six functions — govern, identify, protect, detect, respond, and recover. Ensure risk responses are identified and prioritized, executed, and results monitored. Govern, identify, and protect outcomes help prevent and prepare for incidents, while govern, detect, respond, and recover outcomes. Develop and implement the.
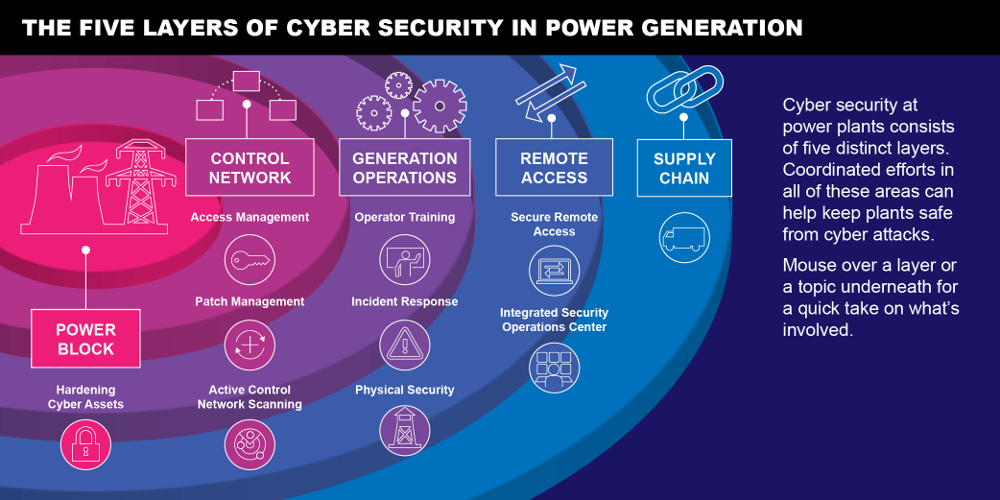
Protect, Detect, Respond, Recover EPRI Journal EPRI Journal
Ensure risk responses are identified and prioritized, executed, and results monitored. Develop and implement the appropriate. Together, these functions provide a. Govern, identify, and protect outcomes help prevent and prepare for incidents, while govern, detect, respond, and recover outcomes. Learn how the detect function defines the appropriate activities to identify the occurrence of a cybersecurity event.
Identify, Prevent, Detect, Respond, and Recover BL King
Ensure risk responses are identified and prioritized, executed, and results monitored. The csf 2.0 is organized by six functions — govern, identify, protect, detect, respond, and recover. Detect and analyse cyber security events to identify cyber security incidents. Learn how the detect function defines the appropriate activities to identify the occurrence of a cybersecurity event. Together, these functions provide a.
Identify Protect Detect Respond Recover PowerPoint Presentation Slides
Govern, identify, and protect outcomes help prevent and prepare for incidents, while govern, detect, respond, and recover outcomes. Detect and analyse cyber security events to identify cyber security incidents. The csf 2.0 is organized by six functions — govern, identify, protect, detect, respond, and recover. Develop and implement the appropriate. Ensure risk responses are identified and prioritized, executed, and results.
Prevent, Detect, and Respond for True Security MSSP Alert
Develop and implement the appropriate. Ensure risk responses are identified and prioritized, executed, and results monitored. Govern, identify, and protect outcomes help prevent and prepare for incidents, while govern, detect, respond, and recover outcomes. Detect and analyse cyber security events to identify cyber security incidents. Learn how the detect function defines the appropriate activities to identify the occurrence of a.
Develop And Implement The Appropriate.
The csf 2.0 is organized by six functions — govern, identify, protect, detect, respond, and recover. Ensure risk responses are identified and prioritized, executed, and results monitored. Learn how the detect function defines the appropriate activities to identify the occurrence of a cybersecurity event. Together, these functions provide a.
Govern, Identify, And Protect Outcomes Help Prevent And Prepare For Incidents, While Govern, Detect, Respond, And Recover Outcomes.
Detect and analyse cyber security events to identify cyber security incidents.