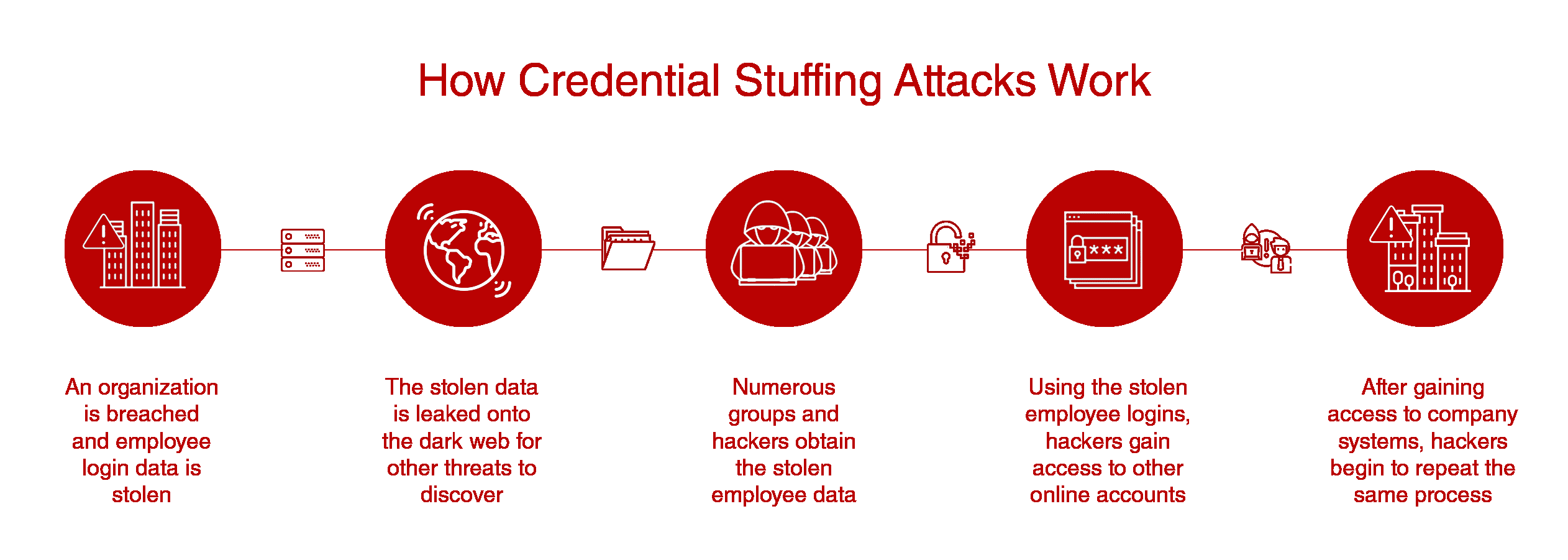
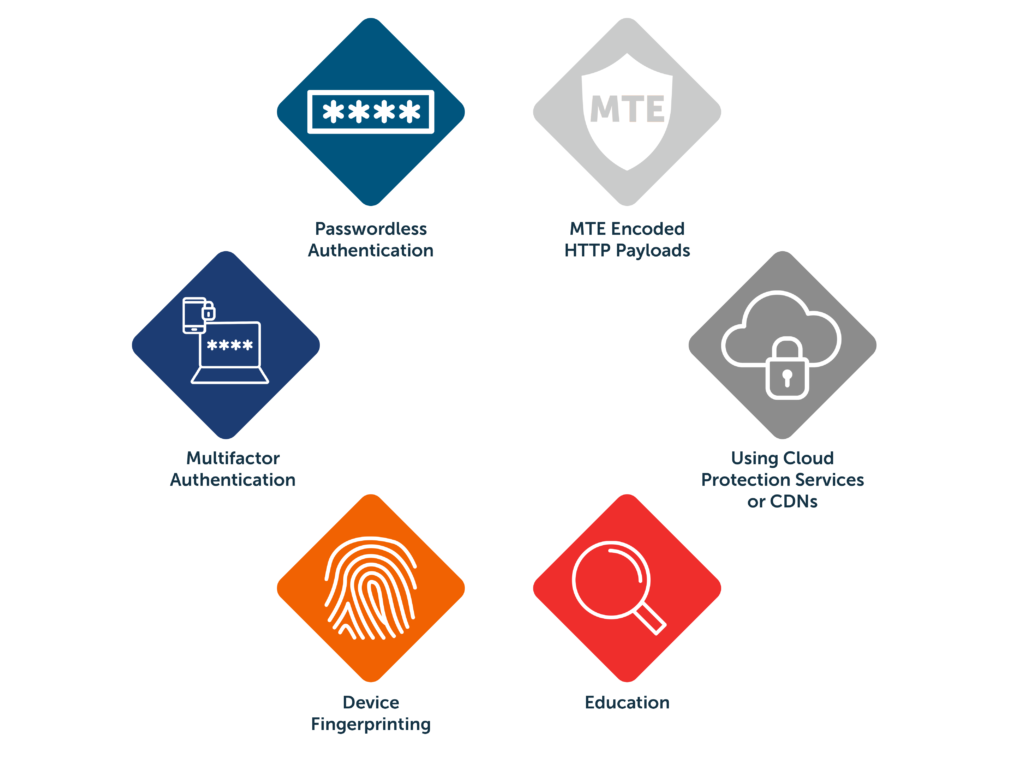
Preventing Credential Stuffing - Here, cybercriminals steal the usernames and. Learn about credential stuffing, how to detect it, and how to prevent it from impacting your organization. Credential stuffing, also called “password stuffing,” occurs when a criminal steals your login credentials for one account. Credential stuffing is a cyberattack method in which attackers use lists of compromised user credentials to breach into a.
Credential stuffing, also called “password stuffing,” occurs when a criminal steals your login credentials for one account. Learn about credential stuffing, how to detect it, and how to prevent it from impacting your organization. Credential stuffing is a cyberattack method in which attackers use lists of compromised user credentials to breach into a. Here, cybercriminals steal the usernames and.
Credential stuffing, also called “password stuffing,” occurs when a criminal steals your login credentials for one account. Credential stuffing is a cyberattack method in which attackers use lists of compromised user credentials to breach into a. Here, cybercriminals steal the usernames and. Learn about credential stuffing, how to detect it, and how to prevent it from impacting your organization.
The WPI Hub Article Identity Theft Credential Stuffing
Learn about credential stuffing, how to detect it, and how to prevent it from impacting your organization. Here, cybercriminals steal the usernames and. Credential stuffing, also called “password stuffing,” occurs when a criminal steals your login credentials for one account. Credential stuffing is a cyberattack method in which attackers use lists of compromised user credentials to breach into a.
What is credential stuffing and are you putting yourself at risk
Credential stuffing is a cyberattack method in which attackers use lists of compromised user credentials to breach into a. Credential stuffing, also called “password stuffing,” occurs when a criminal steals your login credentials for one account. Learn about credential stuffing, how to detect it, and how to prevent it from impacting your organization. Here, cybercriminals steal the usernames and.
Proactive Tips for Preventing Credential Stuffing Attacks Lazarus
Learn about credential stuffing, how to detect it, and how to prevent it from impacting your organization. Here, cybercriminals steal the usernames and. Credential stuffing is a cyberattack method in which attackers use lists of compromised user credentials to breach into a. Credential stuffing, also called “password stuffing,” occurs when a criminal steals your login credentials for one account.
Credential Stuffing Attacks How to Protect Your Web App from Bots
Credential stuffing is a cyberattack method in which attackers use lists of compromised user credentials to breach into a. Learn about credential stuffing, how to detect it, and how to prevent it from impacting your organization. Credential stuffing, also called “password stuffing,” occurs when a criminal steals your login credentials for one account. Here, cybercriminals steal the usernames and.
Credential stuffing What it is and how to prevent it NordVPN
Credential stuffing is a cyberattack method in which attackers use lists of compromised user credentials to breach into a. Credential stuffing, also called “password stuffing,” occurs when a criminal steals your login credentials for one account. Here, cybercriminals steal the usernames and. Learn about credential stuffing, how to detect it, and how to prevent it from impacting your organization.
ONDEMAND WEBINAR Preventing Credential Stuffing Attacks
Credential stuffing, also called “password stuffing,” occurs when a criminal steals your login credentials for one account. Here, cybercriminals steal the usernames and. Credential stuffing is a cyberattack method in which attackers use lists of compromised user credentials to breach into a. Learn about credential stuffing, how to detect it, and how to prevent it from impacting your organization.
The Anatomy of Credential Stuffing Attacks
Learn about credential stuffing, how to detect it, and how to prevent it from impacting your organization. Credential stuffing, also called “password stuffing,” occurs when a criminal steals your login credentials for one account. Here, cybercriminals steal the usernames and. Credential stuffing is a cyberattack method in which attackers use lists of compromised user credentials to breach into a.
Preventing credential stuffing attacks with IPinfo Use Cases IPinfo
Credential stuffing, also called “password stuffing,” occurs when a criminal steals your login credentials for one account. Credential stuffing is a cyberattack method in which attackers use lists of compromised user credentials to breach into a. Learn about credential stuffing, how to detect it, and how to prevent it from impacting your organization. Here, cybercriminals steal the usernames and.
What is credential stuffing and are you putting yourself at risk
Learn about credential stuffing, how to detect it, and how to prevent it from impacting your organization. Here, cybercriminals steal the usernames and. Credential stuffing is a cyberattack method in which attackers use lists of compromised user credentials to breach into a. Credential stuffing, also called “password stuffing,” occurs when a criminal steals your login credentials for one account.
Credential Stuffing Breach Secure Now!
Credential stuffing, also called “password stuffing,” occurs when a criminal steals your login credentials for one account. Here, cybercriminals steal the usernames and. Credential stuffing is a cyberattack method in which attackers use lists of compromised user credentials to breach into a. Learn about credential stuffing, how to detect it, and how to prevent it from impacting your organization.
Credential Stuffing, Also Called “Password Stuffing,” Occurs When A Criminal Steals Your Login Credentials For One Account.
Credential stuffing is a cyberattack method in which attackers use lists of compromised user credentials to breach into a. Here, cybercriminals steal the usernames and. Learn about credential stuffing, how to detect it, and how to prevent it from impacting your organization.