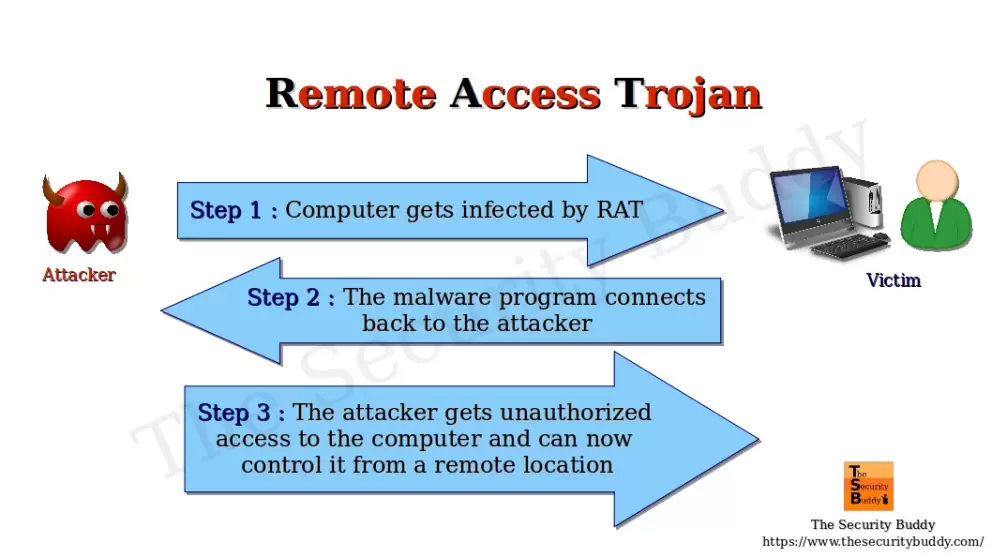
Way To Prevent A Rat Attack Network - Rat prevention, when done correctly, can be an effective way to secure networks and systems. Here are several ways a rat attack can endanger individual users, organizations, or even entire populations: It requires education about cyber threats ,. Cyberattackers use a type of malware tool such as remote access trojans (rats) to infiltrate a network infrastructure to. As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of.
As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of. Cyberattackers use a type of malware tool such as remote access trojans (rats) to infiltrate a network infrastructure to. Here are several ways a rat attack can endanger individual users, organizations, or even entire populations: It requires education about cyber threats ,. Rat prevention, when done correctly, can be an effective way to secure networks and systems.
Here are several ways a rat attack can endanger individual users, organizations, or even entire populations: As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of. It requires education about cyber threats ,. Cyberattackers use a type of malware tool such as remote access trojans (rats) to infiltrate a network infrastructure to. Rat prevention, when done correctly, can be an effective way to secure networks and systems.
3 Easy Ways to Prevent a Rat Infestation wikiHow
As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of. Rat prevention, when done correctly, can be an effective way to secure networks and systems. Cyberattackers use a type of malware tool such as remote access trojans (rats) to infiltrate a network infrastructure to. It requires education about cyber.
Meme Deck Rat Attack Team Leviathan Gaming
As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of. Cyberattackers use a type of malware tool such as remote access trojans (rats) to infiltrate a network infrastructure to. Rat prevention, when done correctly, can be an effective way to secure networks and systems. It requires education about cyber.
4 Ways to Prevent Rat Bite Fever wikiHow
It requires education about cyber threats ,. Rat prevention, when done correctly, can be an effective way to secure networks and systems. Cyberattackers use a type of malware tool such as remote access trojans (rats) to infiltrate a network infrastructure to. Here are several ways a rat attack can endanger individual users, organizations, or even entire populations: As a rat.
overview for Rat_Attack_
Cyberattackers use a type of malware tool such as remote access trojans (rats) to infiltrate a network infrastructure to. As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of. Rat prevention, when done correctly, can be an effective way to secure networks and systems. It requires education about cyber.
3 Easy Ways to Prevent a Rat Infestation wikiHow
It requires education about cyber threats ,. Rat prevention, when done correctly, can be an effective way to secure networks and systems. Cyberattackers use a type of malware tool such as remote access trojans (rats) to infiltrate a network infrastructure to. As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or.
4 Ways to Prevent Rat Bite Fever wikiHow
Here are several ways a rat attack can endanger individual users, organizations, or even entire populations: It requires education about cyber threats ,. Cyberattackers use a type of malware tool such as remote access trojans (rats) to infiltrate a network infrastructure to. Rat prevention, when done correctly, can be an effective way to secure networks and systems. As a rat.
Zombie rat attack 1235192 Vector Art at Vecteezy
Here are several ways a rat attack can endanger individual users, organizations, or even entire populations: Cyberattackers use a type of malware tool such as remote access trojans (rats) to infiltrate a network infrastructure to. It requires education about cyber threats ,. As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone.
RAT Attack That Deploys Two Trojans
It requires education about cyber threats ,. Rat prevention, when done correctly, can be an effective way to secure networks and systems. Here are several ways a rat attack can endanger individual users, organizations, or even entire populations: As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of. Cyberattackers.
Rat Attack (November, 1998) R Retromags Community
Here are several ways a rat attack can endanger individual users, organizations, or even entire populations: Cyberattackers use a type of malware tool such as remote access trojans (rats) to infiltrate a network infrastructure to. Rat prevention, when done correctly, can be an effective way to secure networks and systems. As a rat gets administrative privileges on the infected computer,.
Rat Attack! Nintendo 64 VideoGameX
Here are several ways a rat attack can endanger individual users, organizations, or even entire populations: Rat prevention, when done correctly, can be an effective way to secure networks and systems. Cyberattackers use a type of malware tool such as remote access trojans (rats) to infiltrate a network infrastructure to. It requires education about cyber threats ,. As a rat.
Cyberattackers Use A Type Of Malware Tool Such As Remote Access Trojans (Rats) To Infiltrate A Network Infrastructure To.
Here are several ways a rat attack can endanger individual users, organizations, or even entire populations: Rat prevention, when done correctly, can be an effective way to secure networks and systems. As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of. It requires education about cyber threats ,.







.jpg.9879a5094c588beda9462c90eadcbe6e.jpg)
